
Recovering Deleted Messages to Help Uncover the Criminal Mindset
This article originally published in Forensic Magazine.
Time to evidence matters, particularly when you are at risk of losing data that could hold the answers you’re seeking in a case. The data must be extracted as quickly as possible, especially when you need to preserve data that is “waiting” to be recovered. This often comes in the form of deleted messages on a device. While the missing data could cause gaps in the evidence that obstructs your investigation, it may be possible to recover the messages with the right tools and techniques.
What Happens to Deleted Messages
Text messages live inside a phone’s database. When messages are deleted by a user, they are moved into the freepages of the database, where they should reside until they are permanently removed. The deleted messages can be recovered from this location, though you might not be able to determine the deletion date.
An important consideration when dealing with deleted messages is the vacuuming of the database, which is when deleted data is purged from the database, either automatically by the provider or with the VACUUM command. Until that happens, the database size remains the same. The key, then, is to get to the evidence as quickly as possible to recover the deleted messages from the freepages of the database.
Recovering these files as soon as possible is crucial, as many modern phones vacuum quickly. Older phones, such as throw-away devices, may retain deleted data for longer, making recovery easier. That said, cloud data can be helpful as backups may contain duplicates of data that has been deleted on the device.
How to Retrieve the Deleted Messages
Using Cellebrite Inseyets Physical Analyzer (Inseyets.PA), you can quickly scan for deleted data in the Analyzed Data model. It will look like the image below. Do note there were no deleted messages on the device being tested, hence we are showing deleted data under Networks and Connections.
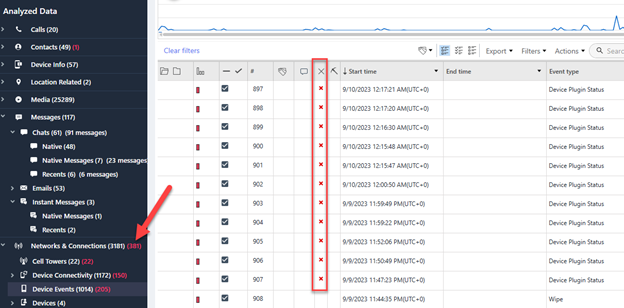
Above, we can see the red items, which are deleted, and the corresponding “x” marks on the right. If one of these deleted items was the key to your investigation, best practices would be to go to the source file, look at the database and ensure the item is indeed deleted and not just carved or enhanced by your digital forensics tool.
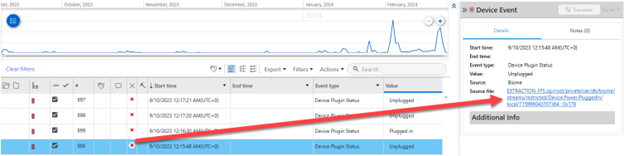
Tools like Physical Analyzer (PA) which offer Deep Carving in SQLite, can help you recover deleted messages that are still present on the device. You can also achieve this by keyword searching in the Hex view inside of PA.
To easily look for deleted messages, we would begin by examining the parsed data to check if any messages flagged as deleted have already been recovered. If they are found, we validate this by clicking on the source file and examining the database for accuracy. On the other hand, if no deleted messages are found in the parsed data, we then explore the database using the Deep Carving or SQLite tool to try and recover any deleted data.
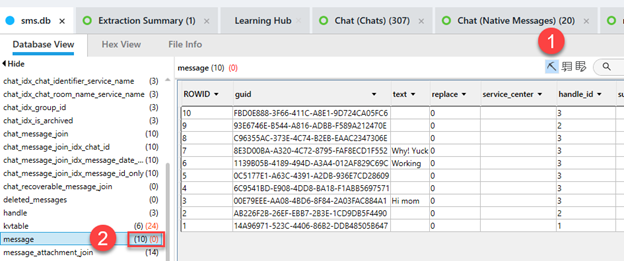
In the example above, ZERO deleted messages were recovered. This could be because VACUUM was run on the database (which is often set by the developers) or because nothing was deleted.
What if You Can’t Recover the Messages?
There may be instances where you’re not able to recover the messages. Maybe the deletion occurred some time ago, and the freepages were deleted as part of the normal database operation. However, you can still get some insights in this scenario.
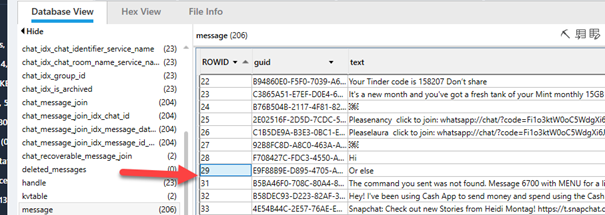
When viewing your database, each message is stored in a sequential order, and as you can see here, entry 30 is missing. Even with deep carving, entry 30 wasn’t recoverable.
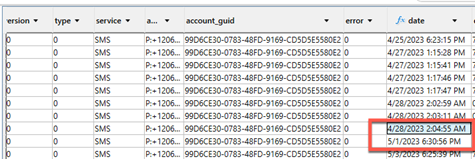
Looking deeper into the database, the message under entry 29 was sent on April 28, 2023, and entry 31 was sent on May 1, 2023. Thus, you can infer that the missing message was sent between April 28 and May 1.
More often than not, deleted messages indicate that someone consciously decided to remove information from their device. This could show the intention to cover up data or eliminate incriminating evidence.
You may not always recover the evidence you need from deleted messages or data, and while you might not get the smoking gun, you could end up with parts of it. It may be circumstantial evidence, yet taken as part of the whole, it could help put context around actions and even be the missing piece that helps solve your case.
About the Authors
Heather Barnhart is the Senior Director of Community Engagement at Cellebrite, a global leader in premier Digital Investigative solutions for the public and private sectors. She educates and advises digital forensic professionals on cases around the globe. For more than 20 years, Heather’s worked on high-profile cases, investigating everything from child exploitation to Osama Bin Laden’s digital media.
As a Product Specialist at Cellebrite, Paul Lorentz regularly assists customers working intricate cases in the lab and thoroughly enjoys guiding and advising examiners – whether it’s working through the data with them or being a sounding board when they need a new perspective. A seasoned law enforcement veteran, Paul takes pride in his craft, knowing the data becomes a silent witness, giving a voice to those who often do not have one.