
Cellebrite Smart Search Security Overview
Security is our highest priority within Cellebrite. This document provides a detailed overview of the security framework, system design, and operational best practices that power Cellebrite Smart Search. In addition, we’re providing details on infrastructure security, procedures, policies, and the data center security standards that our infrastructure providers share.
Key Takeaways
- Security is one of the highest priorities for Smart Search and that’s why it was built according to the principles of Security by Design (the principle that Security is built into the product from day 1 and not as an addition) and Zero Trust (the principle assumes that every interaction is “untrusted” and should be secure and verified).
- Smart Search adheres to the SOC 2 trust services criteria for security in confidentiality and is in the process of undergoing a SOC 2-Type 1 assessment. Smart Search is aligned to UK Cloud Security Principles.
- Smart Search ensures that data protection is at its core, with encryption for both data in transit and data at rest.
- Smart Search a has 99.95% up-time Service Level Agreement (SLA) supported by a 24/7
Network Operations Center and Security Operations Center.
Certification and Compliance
ISO 27001
Cellebrite and all its solutions are certified under ISO 27001, the global standard for IT security management policies, which is a framework of policies and procedures that includes people, processes, and IT systems. The certification means that Cellebrite meets the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS).
ISO 27017
Cellebrite and all its solutions are certified under ISO 27017, the global security standard developed for cloud service providers and users to make a safer cloud-based environment and reduce the risk of security problems. ISO/IEC 27017 provides guidelines for information security controls applicable to the use of cloud services by providing an additional implementation guidance for 37 controls specified in ISO/IEC 27002 and 7 additional controls related to cloud services.
SOC 2
Smart Search is in the process of performing a SOC 2 Type 1 assessment. SOC 2 is the de facto standard attestation of security control design for Software as a Service (SaaS) application. You can rest assured that strict controls are in place to keep your data safe. A SOC 2 Type 2 assessment is planned for 6 months after obtaining SOC2 Type 1.
UK Cloud Security Principles
Smart Search adheres to the Cloud Security Guidance and the 14 Cloud Service Principles defined by the National Cyber Security Centre.
European Union General Data Protection Regulation (GDPR)
Cellebrite maintains compliance with the EU GDPR and complies with the EU-U.S. and Swiss-U.S. Privacy Shield Frameworks as set forth by the U.S. Department of Commerce regarding the collection, use, and retention of personal data transferred from the European Union and Switzerland.
Smart Search Terms of Service
Smart Search is governed by the SaaS Terms of Service. See the Terms of Service at https://legal.cellebrite.com/Cellebrite-SaaS-Terms-of-Service-October-18-2021.htm
Privacy Statement
Cellebrite has a defined Privacy Policy. Read the policy at https://cellebrite.com/en/privacy-statement/
Data Center Security
Amazon Web Services (AWS) is a best-in-class cloud computing provider that delivers an infrastructure that is at least 99.99% available. Smart Search is hosted in AWS GovCloud (US) and AWS Europe (London). Leveraging a provider like AWS ensures that Smart Search is using a highly available and highly secure underpinning infrastructure.
AWS GovCloud provides secure cloud hosting services designed for FedRAMP High baseline; the DOJ’s Criminal Justice Information Systems (CJIS) Security Policy; U.S. International Traffic in Arms Regulations (ITAR); Export Administration Regulations (EAR); Department of Defense
(DoD) Cloud Computing Security Requirements Guide (SRG) for Impact Levels 2, 4, and 5; FIPS 140-2; IRS- 1075; and other compliance standards. Refer to AWS for more information on AWS GovCloud (US).
AWS Europe provides a secure cloud hosting environment conforming to ISO 27001, PCI DSS
Level 1, Cloud Security Alliance (CSA), GDPR, System and Organization Controls (SOC), the NCSC UK’s Cloud Security Principles, and more compliance standards. Refer to the AWS Compliance Center for resources on the AWS Great Britain environment.
Smart Search Architecture
The following diagram provides an overview of Cellebrite Smart Search SaaS architecture.
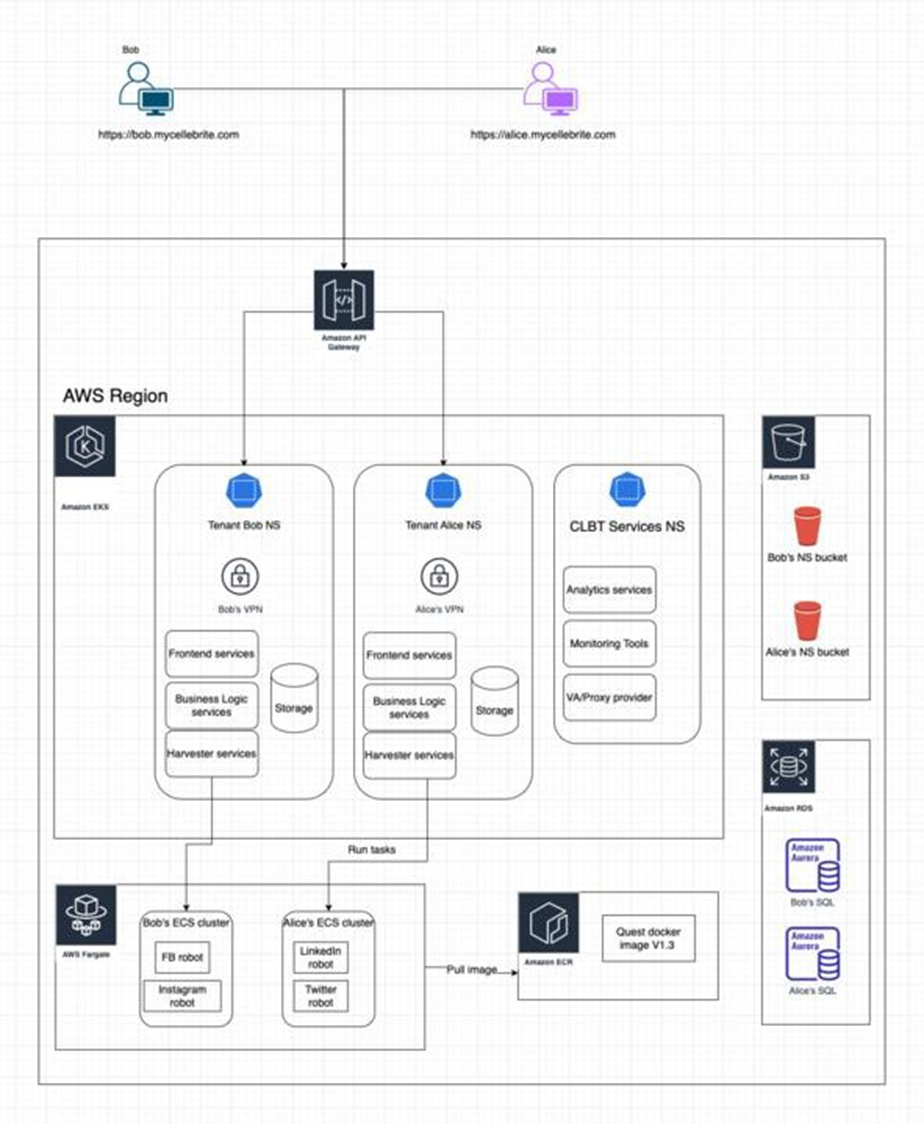
Application and Data Security
Data in Transit
Smart Search uses TLS 1.2 and TLS 1.3 with high-grade ciphers ensuring that all traffic is securely encrypted in transit. Endpoints physically reside in AWS data centers or the Imperva network and are protected from physical access.
Perimeter Security
Smart Search is a Cellebrite solution that is deployed in the Cellebrite AWS environment. Cellebrite employs a multi-layered security approach to safeguard its AWS environments comprised of four defense layers. This solution is part of Cellebrite’s defense-in-depth strategy.
The initial layer utilizes a distributed cloud service that routes all application traffic through robust external scrubbing services that provide advanced security controls, including DDoS protection, anti-bot services, and advanced web application protection. The second layer serves as a central security point, protecting all accounts and preventing unauthorized access to Cellebrite’s AWS environment. It enforces policies, access restrictions, and monitoring while offering advanced web application firewall capabilities, such as protection against injection attacks, cross-site scripting, and SQL injection. The third layer deploys agile, app-centric security components in front of each microservice, utilizing advanced web application firewall capabilities like rate limiting, bot protection, IP reputation services, and schema validation to thwart suspicious activity and unauthorized access. Additionally, this layer ensures that all requests are authenticated and authorized before reaching the microservice, which provides an extra layer of protection. The fourth and final layer is the zero-trust layer, delivering granular, fine-grained access control to each service. It ensures protection against internal and external attacks, ensuring that each service is fortified against all threats.
By deploying these multiple layers of security, Smart Search provides a secure environment for our AWS deployments, guaranteeing the integrity and confidentiality of client data.
Asset Protection and Resilience
With Smart Search, you choose the region in which you want your data to reside, to meet your compliance and jurisdiction needs, which dictates where your data is stored, processed, and managed.
All customer data at rest, such as evidence files, are securely stored in Smart Search using tenant- specific S3 storage using 256-bit AES encryption keys. Encryption keys are securely managed and are
unique per customer. Access to customer data is restricted by permissions to the specific object storage bucket and the relevant decryption key. This protects access to customer data and ensures that only authorized clients can access and process the data. Data resilience ensures that data at rest is stored in multiple availability zones. The availability zones never span across regions, ensuring Smart Search compliance with data governance laws.
Cellebrite regularly backs up Smart Search customer data to ensure data recovery. Backups are appropriately protected, ensuring only authorized individuals can access the protected data and that
backup data is encrypted. Backups are stored in multiple availability zones as an added layer of protection; if a data center fails, your data is still safe.
Cellebrite has sanitization processes that ensure that your data is permanently deleted should you choose to leave the solution.
Cellebrite uses monitoring systems to identify performance issues and detect problems in the Smart Search solution. The monitoring tools are integrated with a 24 / 7/ 365 alerting system to ensure the relevant teams are notified of any issues in the solution.
To ensure the secure and reliable management of secrets within our system, we have implemented a multi-faceted approach that combines the use of Kubernetes secrets, AWS Secret Manager, and AWS Parameter Store. Kubernetes secrets provide a secure and reliable way to store and manage sensitive information, such as passwords, API keys, and certificates within our cluster, while AWS Secret Manager and AWS Parameter Store allow us to store and manage secrets outside of the Kubernetes cluster with additional functionality such as rotation and auditing.
Furthermore, we have implemented a rigorous IAM policy that enforces the principle of least privilege for each service by providing a separate IAM role. For AWS resources, we use a unique IAM role to ensure that each service has access only to the resources it requires, reducing the risk of a security breach due to compromised credentials. If we are not using AWS resources, we have implemented a separate database user for each service, which ensures each service has access only to the databases it requires and nothing more. This approach provides a high level of security and protection against potential security threats, ensuring that our secrets are securely managed, and access to them is strictly controlled.
Smart Search is backed by a 99.95% uptime SLA which means that it will be there when you need it. Supporting transparency of the solution, Smart Search leverages a status/trust site to reflect the status of the solution and to communicate pending maintenance to our customers. All customers can subscribe to this status page to be notified of maintenance or issues with the solution. Visit the status page and subscribe today at: https://status.cellebrite.cloud.
Separation between Tenants
Smart Search is a multi-tenant solution. Traffic & Data isolation and segregation between tenants is designed and enforced from the ground up. Each data object stored in the system is confined to the relevant tenant scope. This allows for strict enforcement of role-based access policies and enforces tenant isolation & segregation. Each tenant’s sub-environment is isolated via multiple abstract layers including network, identity, object stores, etc.
Smart Search employs Amazon Elastic Kubernetes Service (EKS) to manage the Kubernetes cluster, providing a reliable and scalable solution for deploying containerized applications. To ensure a secure
and isolated multi-tenant environment, Cellebrite has implemented a network architecture based on security groups and network policies using Calico, a popular open-source networking and network security solution for Kubernetes. This approach allows tenants to communicate only with authorized resources, providing a high level of security and isolation within the cluster. By leveraging these technologies together, we have created a secure and efficient environment that enables multiple teams or customers to share the same Kubernetes cluster while ensuring the confidentiality and integrity of their resources and data.
Additionally, to ensure the multi-tenant environment provides a high level of data segregation and security, Cellebrite has implemented measures to store each tenant’s data in separate and secure resources. Specifically, we have created different resources such as distinct Amazon S3 buckets and databases for each tenant. This approach guarantees that each tenant’s data is stored separately and is only accessible by authorized users. We have also enforced strict access controls to these resources by employing IAM policies that restrict access to only the necessary users and resources, thus reducing the likelihood of unauthorized access or data breaches. These measures provide a strong level of data security and privacy to our tenants, ensuring that their data remains confidential and secure.
The principle of ‘least privilege’ and ‘separation of duties’ dictates access control policies.
Similarly, “least privilege” and “separation of duties” concepts are also enforced within Cellebrite by cloud administrators. The tenant setup is deployed using IaaS (Infrastructure as a Service) technology. The IaaS cannot break the tenant isolation concept, which is enforced and managed by the Cellebrite Landing Zone enterprise administrators. This implementation is based on the AWS Landing Zone solution that establishes and implements the security baseline for our SaaS infrastructure.
The Cellebrite Security Landing Zone covers the following topics:
- AWS Organization and Accounts Structure
- Identity and Access Management
- Logging and Monitoring
- Infrastructure Security
- Data Protection
- Incident Response
- Cost Governance and Control
- Shared Services
Governance Framework
Cellebrite has a security governance framework that coordinates and directs the management of Smart Search and the information within it. The Chief Information Security Officer owns the Cellebrite Information Security Program. The Information Security Committee (ISC) governing the Information Security Policy, consists of a cross-functional team representing operational groups across the organization and is led by senior management. All employees are required to understand, agree, and
adhere to the Information Security Policy. The Information Security Policy is reviewed and updated annually.
Operational Security
All changes are logged in our source code repository. We leverage industry standard deployment tools to provision Smart Search ensuring auditable and the use of standard accepted configurations.
Cellebrite has a stringent software release policy. Notifications on pending releases are updated on the public status site (https://status.cellebrite.cloud) before the release, where possible. Urgent or critical releases may bypass this notification if deemed required.
The Cellebrite Threat Ops team continuously monitors product logs, infrastructure operations, and systems audit logs in our internal SIEM (Security Information and Event Management) to promptly detect and react to potential incidents. Cellebrite security has established comprehensive policies and a strategy to respond to, notify, and remediate security incidents. Cellebrite runs continuous and automated vulnerability scans for the Smart Search assets, prioritizes vulnerability fixes, and quickly releases patches.
Our SOC (Security Operations Center) is staffed with highly qualified and experienced Security Analysts who work to keep the environments secure. Cellebrite has a detailed incident response policy and plan. The approach ensures that security incidents are identified, contained, investigated, and remedied.
There are also processes for documentation, reporting security incidents internally and externally, and a root cause analysis to identify and communicate improvements and actions that need to be made after every security incident.
Security solutions have been put in place as part of our multi-layer protection approach for web and API traffic protection. Leveraging the “Defense in Depth” principle, Cellebrite protects Smart Search with multiple levels of protection including anti-DDoS protection, advanced rate limiting solutions, and bot protection all supported by next-gen Web Application Firewalls and additional cloud-native solutions for comprehensive overall web protection. These solutions protect the integrity of the web and API traffic processed by Smart Search and prevent availability attacks on the system.
Personnel security
All employees working on Smart Search are required to complete and comply with mandatory security training, have undergone background checks, and are educated on supporting Smart Search and working with underpinning contract providers such as AWS.
Secure Development
Cellebrite uses policies and procedures to guide our software development lifecycle (SDLC). The Secure- SDLC approach we employ ensures that secure development activities, such as security risk analysis,
code reviews, static code analysis, and penetration testing are integral to the development effort. Quality Assurance is done by manual and automated QA processes. Additionally, routine performance testing is conducted to ensure a performant application.
The Secure-SDLC design leverages multiple security technologies and processes to ensure that the application is developed and managed to significantly reduce security risks. Cellebrite uses the “Security by design” approach by adopting the “Shift Left” practice and embedding security throughout all phases of the development lifecycle to detect and mitigate security issues at early stages.
Additionally, threat modeling is conducted to identify and reduce risk. As application risks are discovered, the risks are quantified, assessed, and mitigated accordingly. Security vulnerability scanners and SCA (Software Composition Analysis) tools are used to scan our infrastructure and application.
Cellebrite also engages external vendors to conduct periodic web penetration tests on all products allowing for third-party attestation of the product security controls.
Only the Site Reliability Engineering (SRE) team (operations) has access to the production environments. There is a clear division between Site Reliability Engineering and Development. Supervised access is given to production systems only as needed and only to specific sections.
We continuously test security to ensure our environment stays secure. Using the Open Web Application Security Project (OWASP), Cellebrite constantly reacts to emerging threats ensuring the safety of customer data. Additionally, we adhere to secure design principles such as “Zero Trust”, “Defense in Depth”, and “Least Privilege.”
Secure User Management
Smart Search entails robust measures to ensure the uncompromising separation of user pools per tenant, thus effectively mitigating any risk of unauthorized access or interference between disparate tenant environments and upholding the utmost confidentiality, availability, and integrity of each tenant’s data and resources.
A Smart Search Administrator configures user Roles and Permissions within the application at the workspace level. Smart Search Administrator users can add users to the system, add additional Administrator users, reset passwords, and manage group permissions for the workspace.
Supply Chain Security
Cellebrite conducts vendor risk assessments to ensure that the solution providers that are part of the Smart Search solution/supply chain are secure and follow best practices wherever possible. Our assessments include questionnaires, a review of their certifications and reports, and, if appropriate, independent assessments.
Identity and Authentication
Smart Search application leverages the modern authentication protocol OIDC (OpenID Connect) together with the authorization code flow.
All Smart Search users access the application using unique per-user credentials and two-factor authentication. Additional authorization layers prevent users from accessing data without proper explicit permissions from organizational administrators. In addition, access control mechanisms are implemented to verify each web request’s session validity and authenticity.
Sessions are established between the browser and Smart Search. All sessions have an inactivity timeout, which forces the user to log in / reauthenticate if no activity is detected for that session.
External Interface Protection
Smart Search protects our interfaces by leveraging web security best practices, including secure headers that protect web sessions and data security. The application uses public and private subnets with enforcing Network Access Controls to manage the traffic. Additionally, sensitive web cookies are protected with relevant security flags such as Http Only, Secure, and SameSite.
Secure Service Administration
Access to the Smart Search network is strictly limited to the Cellebrite Site Reliability Engineering team. The SRE team functions as Operations for the solution. Cellebrite policy and technical controls ensure that VPN access to the Smart Search networks comes from company-approved assets that are running company-controlled endpoint protection services and are managed devices. Access to the production environment is centrally logged and scrutinized.
Audit Information for Users
Smart Search application Administrators have access to the end-user application logs so that they can monitor end-user activity. In addition to browsing the logs from the application, the logs can be exported to a variety of formats, so that you can use other log analysis tools, if desired.
Security Questions
For security questions and inquiries, please get in touch with the Cellebrite Support Team: https://cellebrite.com/en/support/