Cellebrite’s CTF 2023 Recap: Answers for Felix’s iPhone Device

We would like to thank everyone who participated in the Capture the Flag event. There were many late evenings and lots of hard work by many people involved. This is Cellebrite’s way of giving back to the community and providing resources to keep learning!
We wanted to provide a walkthrough on how we arrived at the answers. There may be situations where we show a method of deriving the answer which may differ from the method you used to get the answer, but this is the beauty of forensics: the paths we take may differ, but the results are the same.
The screenshots below come from PA Ultra, so you may or may not have a similar view depending on what tool(s) you used during the competition.
The Backstory/Scenario:
As a recap, terror attacks were planned for Southport, NC in June of 2023. Russell, the primary suspect, lives locally in that area and seems to have been introduced to Abe via Sharon. Russell and Sharon go way back, and she seems to be the linchpin who tied Abe to Russell. So, who is Abe? How is he involved with Felix? Why would Felix be feeding a US person with information on nuclear power plants and weapons? We intend to leave this scenario open-ended but wanted to give you some backstory.
Felix’s iPhone Questions:
Felix 01 – Voicemail – Level 1 (10 points)
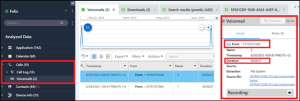
Felix received a voicemail from +1-416-435-5684. How many seconds in length was the voicemail message?
Answer: 27 (twenty-seven)
This information can be quickly located in PA by navigating to the Calls model under Analyzed Data, and then selecting Voicemails.
Felix 02 – Picture – Level 1 (10 points)
Please look at the following image: IMG_0026.HEIC. How many times do you see this picture on the device (including thumbnails)?
Answer: 5 (five)
Using the search function in the upper lefthand corner to search for IMG_0026.HEIC will return five results.
Felix 03 – Confirmation – Level 1 (10 points)
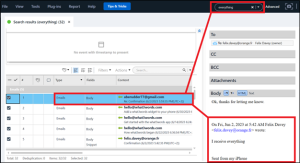
Felix confirmed receiving “everything.” When Felix sent the confirmation, which account did he sent it from?
Answer: felix.davey@orange.fr
Felix sent Abe an email that stated, “I receive everything.” As with the previous question, utilizing PA’s search function comes in handy. Search for “everything” and five hits are returned, two of which return the content of Felix’s email.
Felix 04 – Photo – Level 1 (10 points)
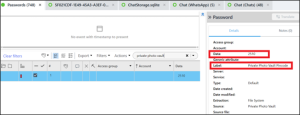
Private Photo Vault is an application that is installed on the phone. What is the passcode to the application?
Answer: 2510
PA is able to provide another quick win here. Navigate to the Analyzed Data tab and select the User Accounts & Details model. Under that model select Passwords.
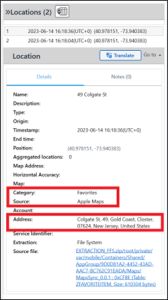
Felix 05 – Location – Level 1 (10 points)
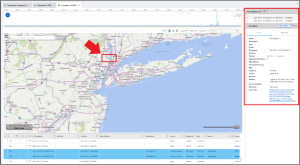
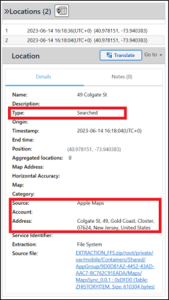
Felix always had an interest in the USA. What application did he use to search for an address in New Jersey USA?
Answer: Apple Maps
Felix searched for 49 Colgate St in New Jersey, and subsequently added it as a Favorite. To see both, open the Locations model in Analyzed Data and zoom in on New Jersey. There are only two locations there, and both are derived from Apple Maps.
Felix 06a – Size – Level 1 (10 points)
What is the size (in bytes) of the ChatStorage.sqlite-wal file? Answer with numeric digit(s) only.
Answer: 0
Felix 06b – Time – Level 2 (30 points)
What is the date and time the -WAL file from Felix 06a committed to the main database?
Answer: 2023-07-01 05:49:55
Since these two questions are related, let’s tackle them together. ChatsStorage.sqlite and the associated -WAL file are found in /private/var/mobile/Containers/Shared/AppGroup/5F021CDF-1E49-45A3-A3EF-02BE149681AC/. The first question is straightforward. Inspecting ChatStorage.sqlite-wal find that it has a size of 0.
Now look at the last modified time of ChatStorage.sqlite and the associated -WAL file. The files share the same last modified time, 2023-07-01 at 05:49:55, which is indicative of commit to ChatStorage.sqlite.
Felix 07 – Size – Level 2 (30 points)
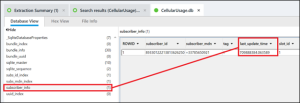
When was the SIM card information on Felix’s phone last updated? (Raw data, not converted)
Answer: 709888384.063589
While this information is not readily available, a quick examination of CellularUsage.db can find it. The database is found in /private/var/wireless/Library/Databases. In the table subscriber_info look for the value in the column last_update_time to find the answer.
Felix 08 – Missing – Level 2 (30 points)
The WhatsApp chat database appears to be missing some chat messages. Assuming the highest number is the last message, how many messages are missing?
Answer: 19 (nineteen)
For this question we revisit the file ChatStorage.sqlite from Felix 06a and 06b. Message information is found in the table ZWAMESSAGE.
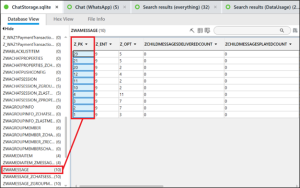
The column Z_PK provides the necessary information. The question tells us to assume that the highest number is the last message. Here, that number is 29. Evaluating that column further finds:
- We have 5 missing messages (between Z_PK 4 and Z_PK 10 ) between 2022-12-01 18:06:00 and 2023-03-31 10:03:42.
- We have another 7 missing messages (between Z_PK 12 and Z_PK 20 ) between 2023-05-19 14:18:08 and 2023-06-03 13:37:43
- We have another 7 missing messages (between Z_PK 21 and Z_PK 29 ) between 2023-06-03 13:37:43 and 2023-07-01 05:41:04
All for a total of nineteen (19).
Felix 09 – Wiped – Level 2 (30 points)
When was Felix’s phone last wiped?
Answer: 2022-12-01 17:16:55
Heather and Ian had an article published on DFIR Review that discussed artifacts related to iOS device wipes, and one of the artifacts they discussed is the answer here. The file .obliterated can be found in /private/var/root/. Look at the last modification time for the answer.
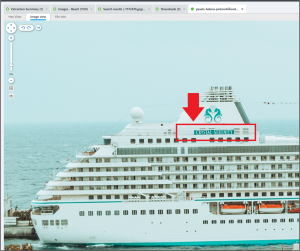
Felix 10 – Cruise – Level 2 (30 points)
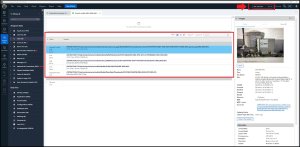
Felix was researching / surveilling a ship as a possible target and downloaded a photo of it. What is the name of the cruise ship?
Answer: Crystal Serenity
There are at least two versions of the photograph of this boat on Felix’s phone, but one is degraded which makes it difficult/impossible to make out the name. There was some browser activity that resulted in the picture of the ship being downloaded. On iOS it is not uncommon for downloaded files to land in iCloud, which is what happened here. So, examining the directory /private/var/mobile/Library/Mobile Documents/ is a good place to start. In that directory path the folder “com~apple~CloudDocs” is present and contains a subdirectory “Downloads,” which contains only one file that starts with “pexels-helena…” The file is a picture that depicts the ship, Crystal Serenity.
Felix 11 – Data – Level 3 (50 points)
Which process on Felix’s phone used the most cellular data (network traffic INTO the device)?
Answer: CumulativeUsageTracker
The file DataUsage.sqlite contains the information needed to answer this question and is found in /private/var/wireless/Library/Databases/. To find the answer open the database, navigate to the table ZLIVEUSAGE, look in the column ZWWANIN, sort the values in the column by amount, and look for the highest number. Here it is 479085390.
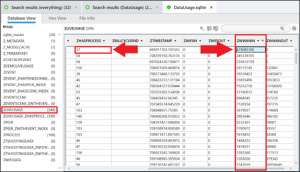
Note the corresponding value in the ZHASPROCESS column is “37.” Next navigate to the table ZPROCESS and locate “37” in the Z_PK column.
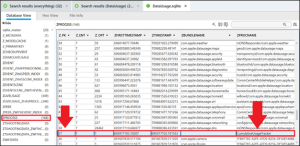
Since we are looking for the process name, we look to the column ZPROCESS name for the answer: CumulaltiveUsageTracker.
Felix 12 – H is mean – Level 3 (100 points)
Felis was referred information about pension reform. What is the SID associated with that artifact?
Answer: c5141308-e98c-11ed-8f70-ea4e37ab9147
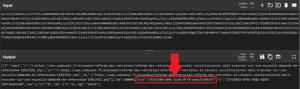
One of (if not the biggest) challenges with this question was figuring out where to start. There is a subtle clue in the question, though: “reform.” Our very own Ian Whiffin took a few standard swings at it and then tried a few outside-of-the-box methods. Eventually, he tried converting the word “reform” into base64 and tried variants (based on spaces/whole words) until he landed at only two hits searching the binary for the string “yZWZvcm.” Doing so in PA yielded only two hits, both of which referred to the same file.
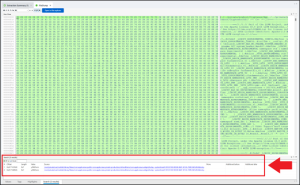
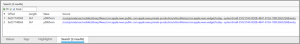
This file, entry, is located in root/private/var/mobile/Library/News/com.apple.news.public-com.apple.news.private-production/referralItems/com.apple.news.widget/today–systemSmall-35F237A0-BD2B-4841-813A-789C26E52EAB/. Once opened, the file is found to contain JSON data. Within it, there is a large blob of bas64 encoded data. CyberChef can be used to decode the base64 blob, which turns out to be a binary property list (bplist) file.
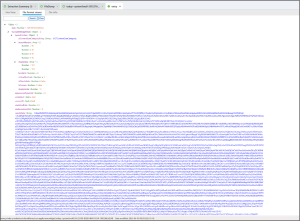
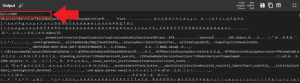
Saving the bplist out and examining it further finds additional base64 encoded blobs within it. Decoding the last blob finds the “sid.”