
Cellebrite’s CTF 2023 Recap: Answers for Russell’s Android Device

We would like to thank everyone who participated in the Capture the Flag event. There were many late evenings and lots of hard work by many people involved. This is Cellebrite’s way of giving back to the community and providing resources to keep learning!
We wanted to provide a walkthrough on how we arrived at the answers. There may be situations where we show a method of deriving the answer which may differ from the method you used to get the answer, but this is the beauty of forensics: the paths we take may differ, but the results are the same.
The screenshots below come from PA Ultra, so you may or may not have a similar view depending on what tool(s) you used during the competition.
The Backstory/Scenario:
As a recap, terror attacks were planned for Southport, NC in June of 2023. Russell, the primary suspect, lives locally in that area and seems to have been introduced to Abe via Sharon. Russell and Sharon go way back, and she seems to be the linchpin who tied Abe to Russell. So, who is Abe? How is he involved with Felix? Why would Felix be feeding a U.S. person with information on nuclear power plants and weapons? We intend to leave this scenario open-ended but wanted to give you some backstory.
Russell’s Android Questions:
Russell 01 – Call – Level 1 (10 points)
Russell got a FaceTime call. When did he join it (UTC)?
Answer: 2023-06-07 23:24:39
Russell received a link for the FaceTime call from Abe via Signal on 2023-06-07 at 22:20:41, and while Russell opened the link, he didn’t join the call right away. Below is the message from Sharon’s phone.
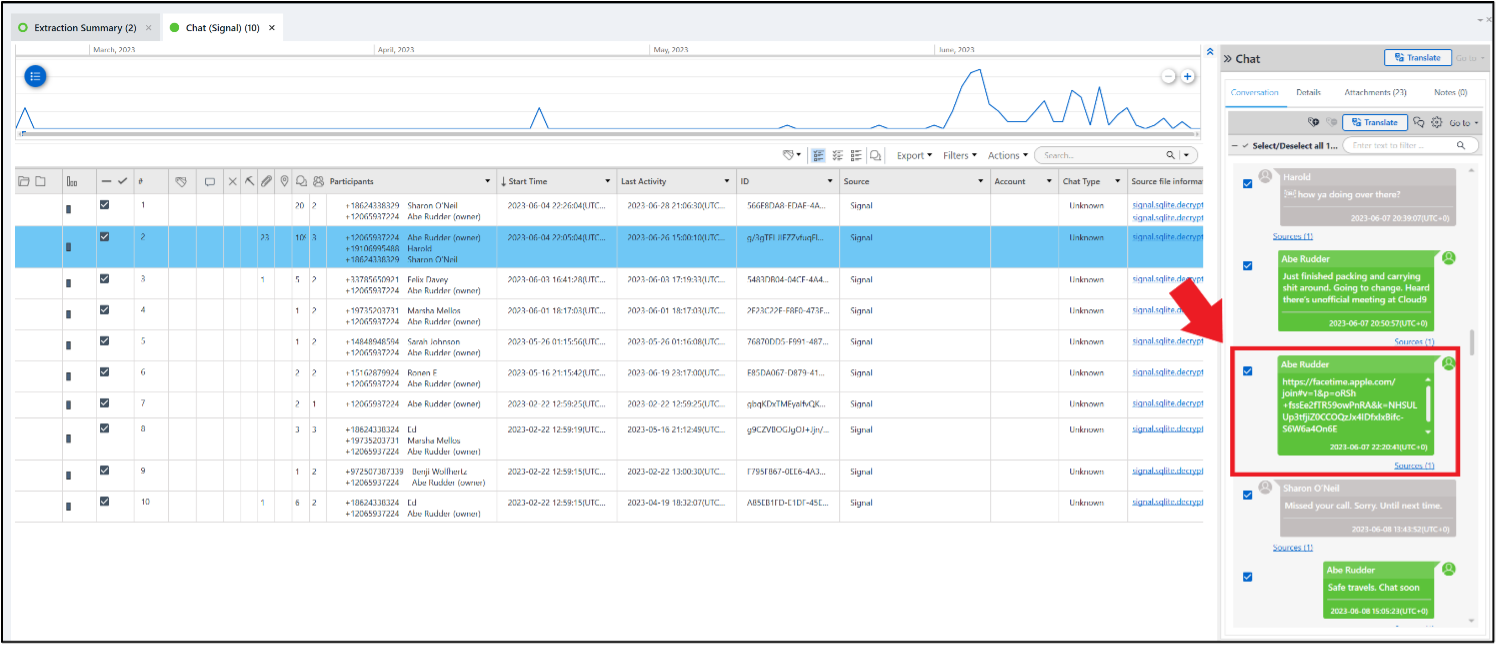
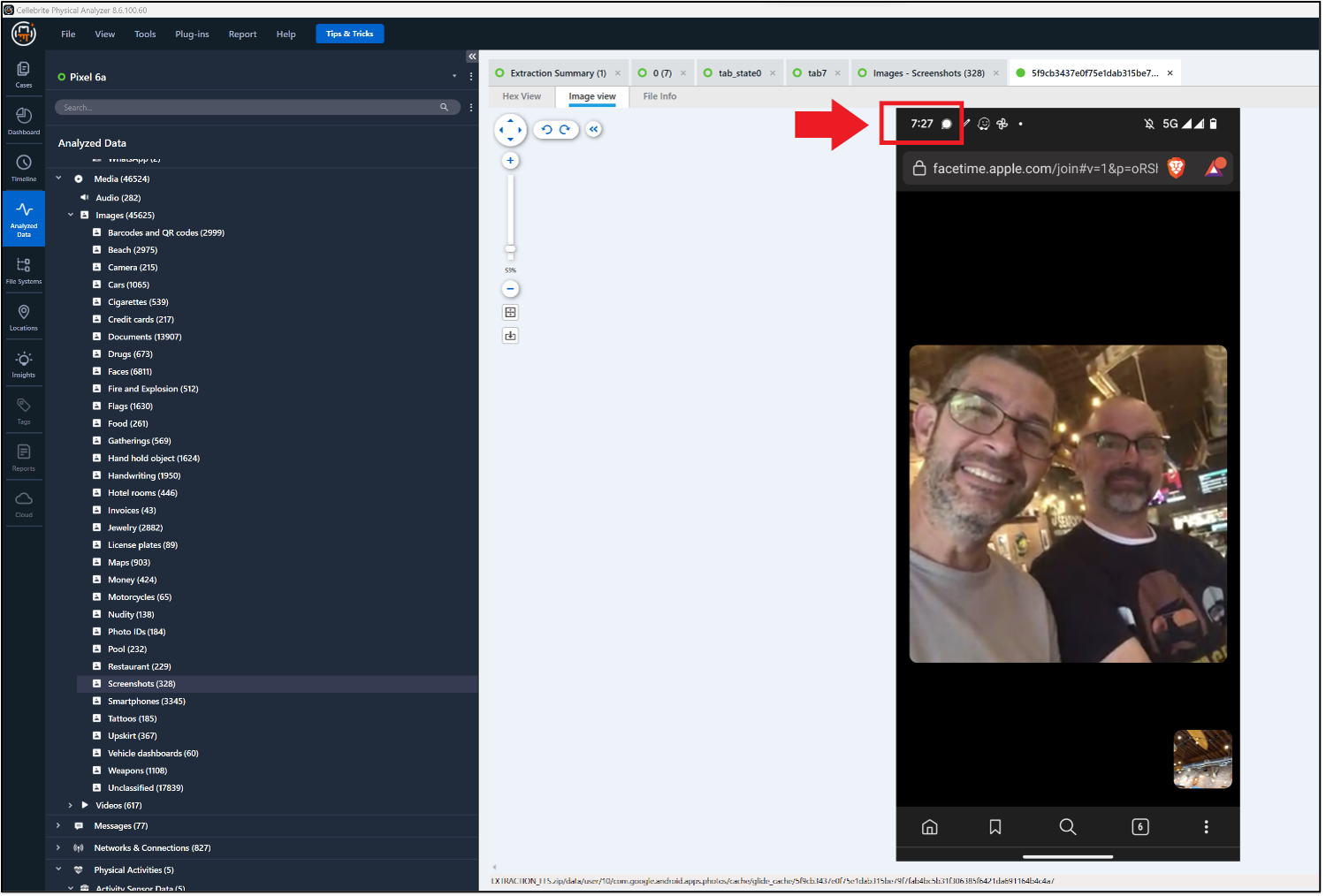
On Russell’s phone, there is a screenshot taken in Brave Browser that shows Ronen (Abe) & Josh (Russell) during the call. The URL in the address bar includes “facetime.apple.com/join…” The time seen in the upper left corner is not correct, though.
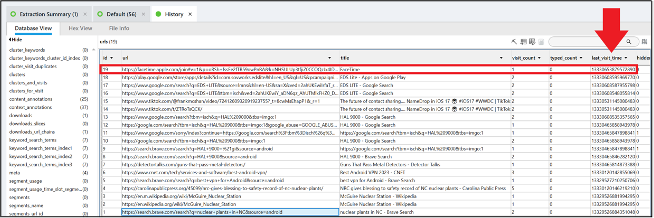
The file History in /data/user/10/com.brave.browser/app_chrome/Default/ contains the needed information in the urls table.
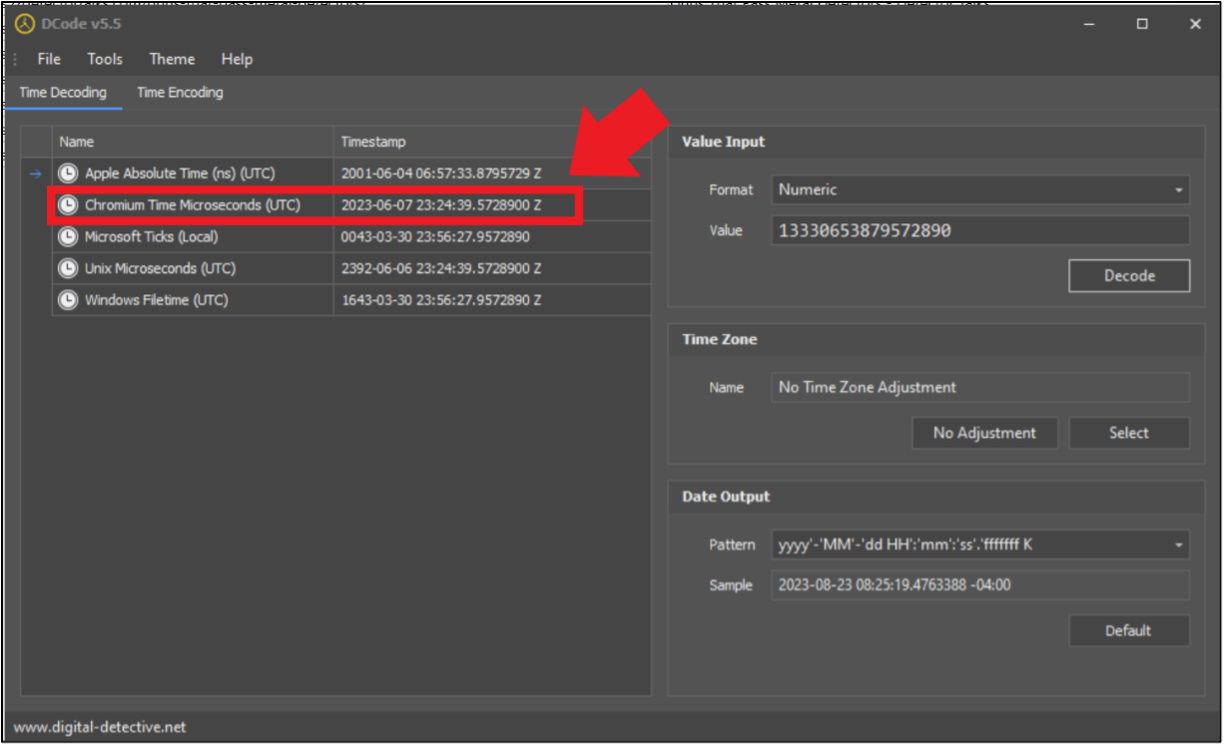
Russell joined the call, and Abe joined shortly thereafter.
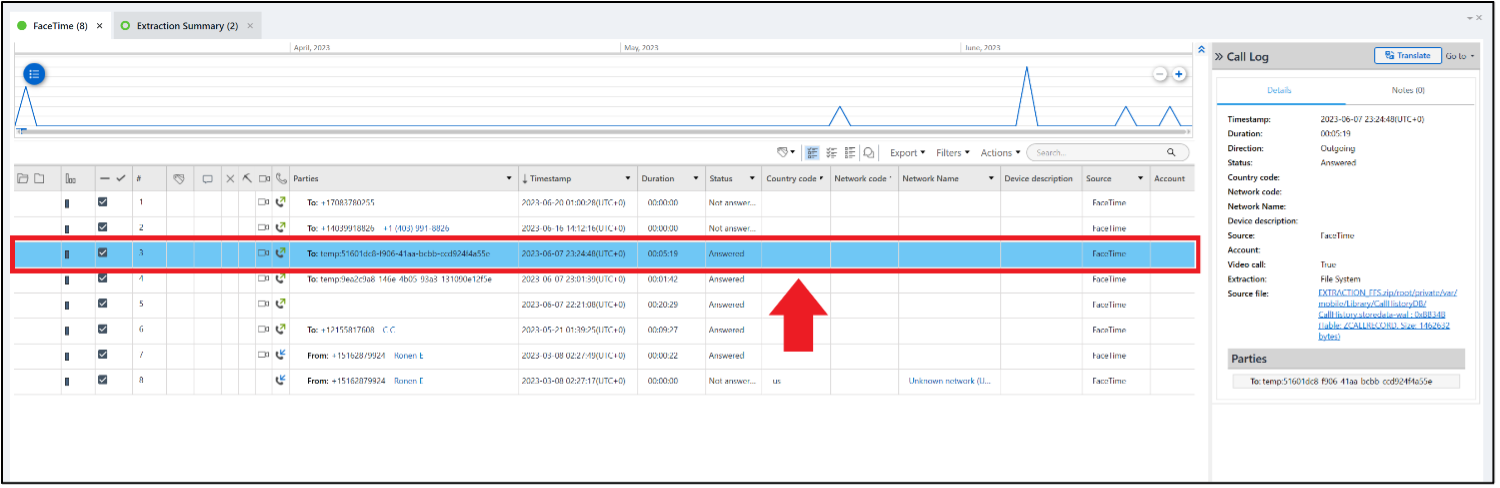
Russell 02 – Bluetooth – Level 1 (10 points)
Which user profile on Russell’s phone last connected to his Bluetooth speaker?
Answer: Profile 0 or 0 as the last profile to connect to the JBL Flip 6 speaker
You need to look in two places, but PA Ultra does parse the needed information. The first place to look is Device Connectivity under Networks & Connections. The last time the speaker connected to the phone was on 2023-06-03 at 17:34:40 UTC.
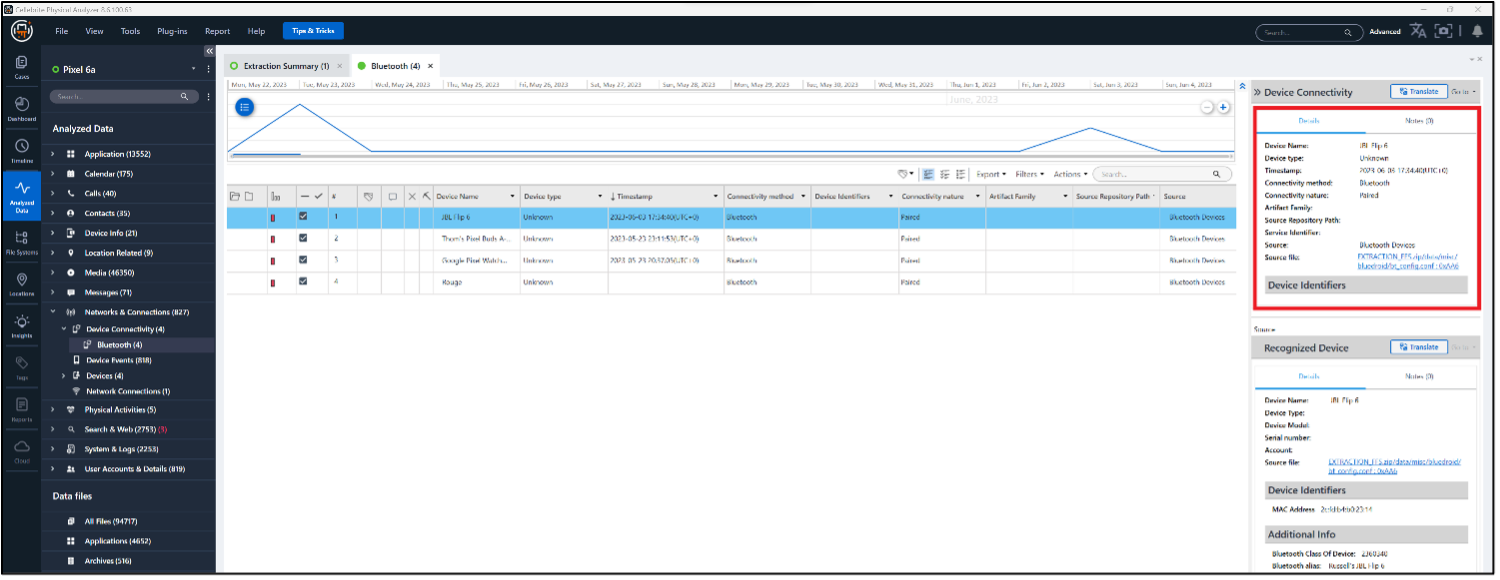
The next item to look at is Device Events, which is also under Networks & Connectivity. The device was unlocked at 2023-06-03 at 17:33:34 UTC, which is just prior to the Bluetooth connection event. The source for this event is Digital Wellbeing, which is found in /data/data/com.google.apps.wellbeing/databases/app_usage. Because there is a second profile on this device, Profile 10, there is a separate version of this file on the phone, but in a different location: /data/user/10/com.google.android.apps.wellbeing/databases/app_usage. For the answer here, the file path does not have “10,” it is simply /data/data/, which indicates Profile 0 unlocked the phone and subsequently connected to the speaker.
Russell 03a – App – Level 1 (10 points)
What app did Russell use to send location information to the group?
Answer: what3words or com.what3words.android
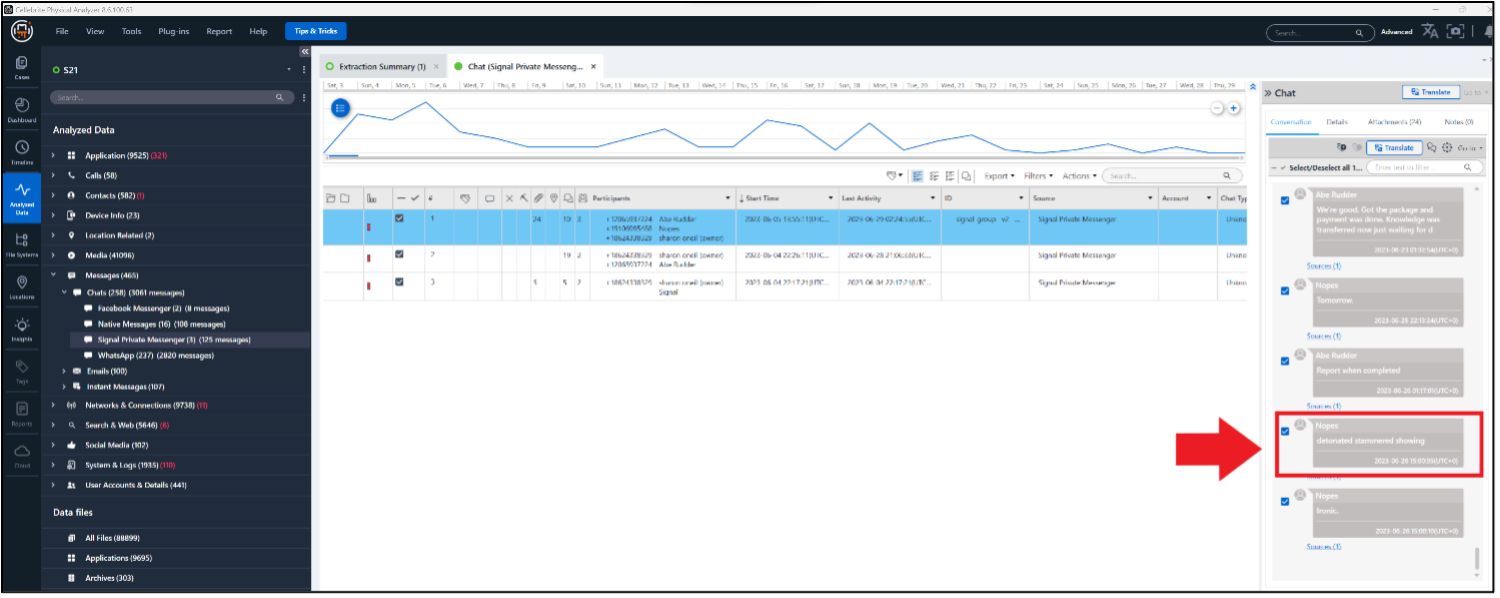
The answer is easily found if you examine Abe or Sharon’s phone. A group message was sent in Signal on 2023-06-26 at 15:00:10 UTC. The message simply states: “detonated stammered showing.” The sending party is “Nope.” On Abe’s phone, it’s “Harold.”
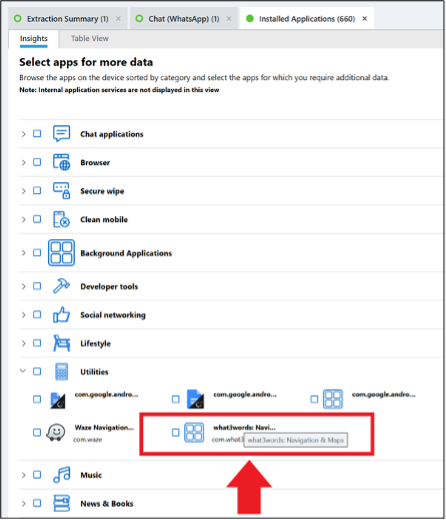
Under Profile 10 the package com.what3words.android is found. Under the Installed Applications model in PA Ultra, that app is listed under Utilities as “what3words: Navigation & Maps.”
Russell 03b – Directions – Level 3 (50 points)
Did Russell get directions to the location described in the previous question (Russell 03a)? If so, when (UTC)?
Answer: 2023-06-26 15:02:42 or 2023-06-26 15-02-42.
This question was hidden from players until Russell 03a was answered correctly. So, if you did not get Russell 03a, you would not have seen it.
The file QafeEcXOSgScVMMQLRC3GA_analytics has the answer. It is a database file found in /data/user/10/com.what3words.android/no_backup/ and is used to track app usage. The table events appear blank in PA Ultra until the pickaxe is used to show recovered records.
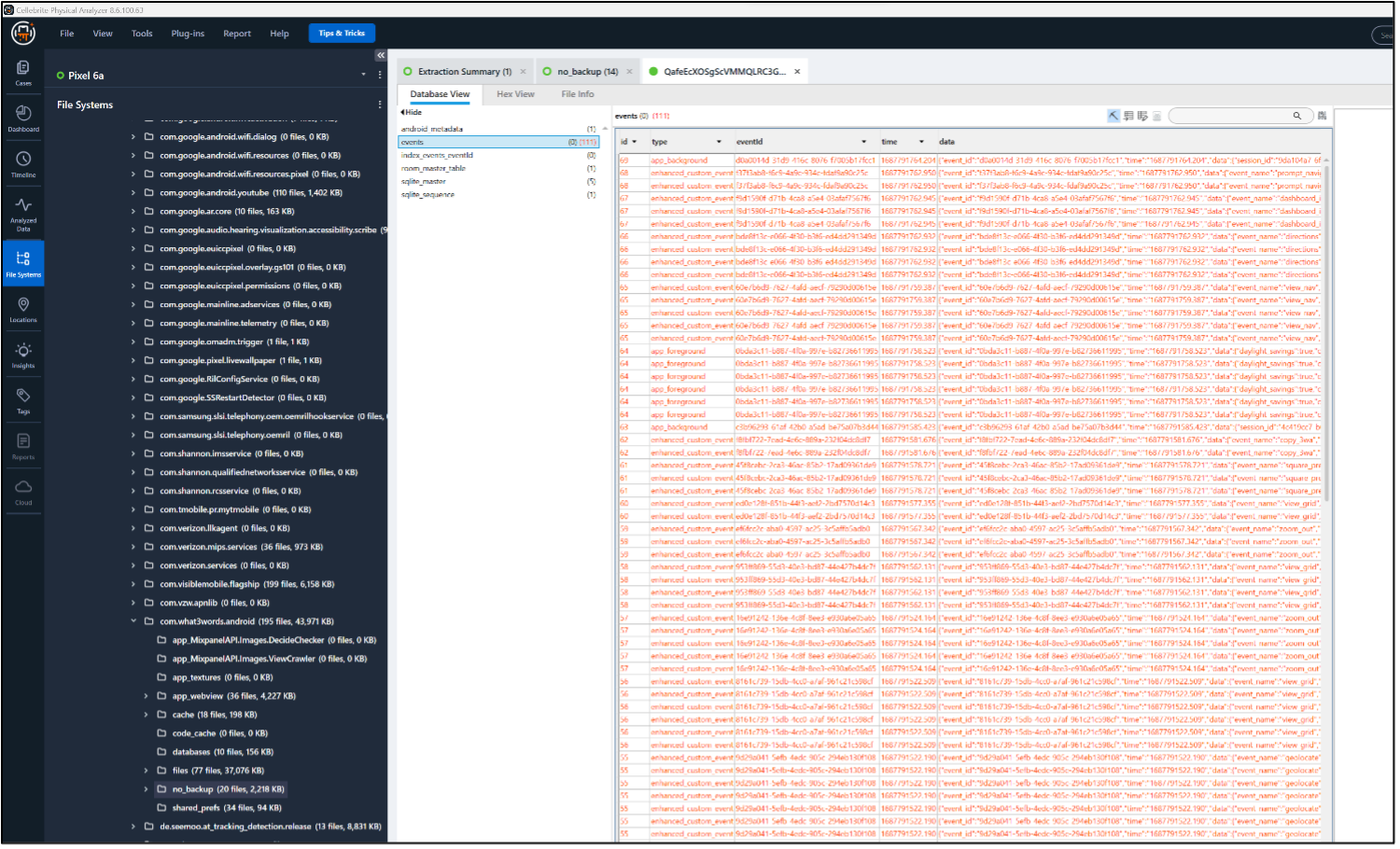
Filtering that table by the word “detonated” find a few records related to the event, including when directions were obtained via Waze: 1687791762.932 (2023-06-26 15:02:42).
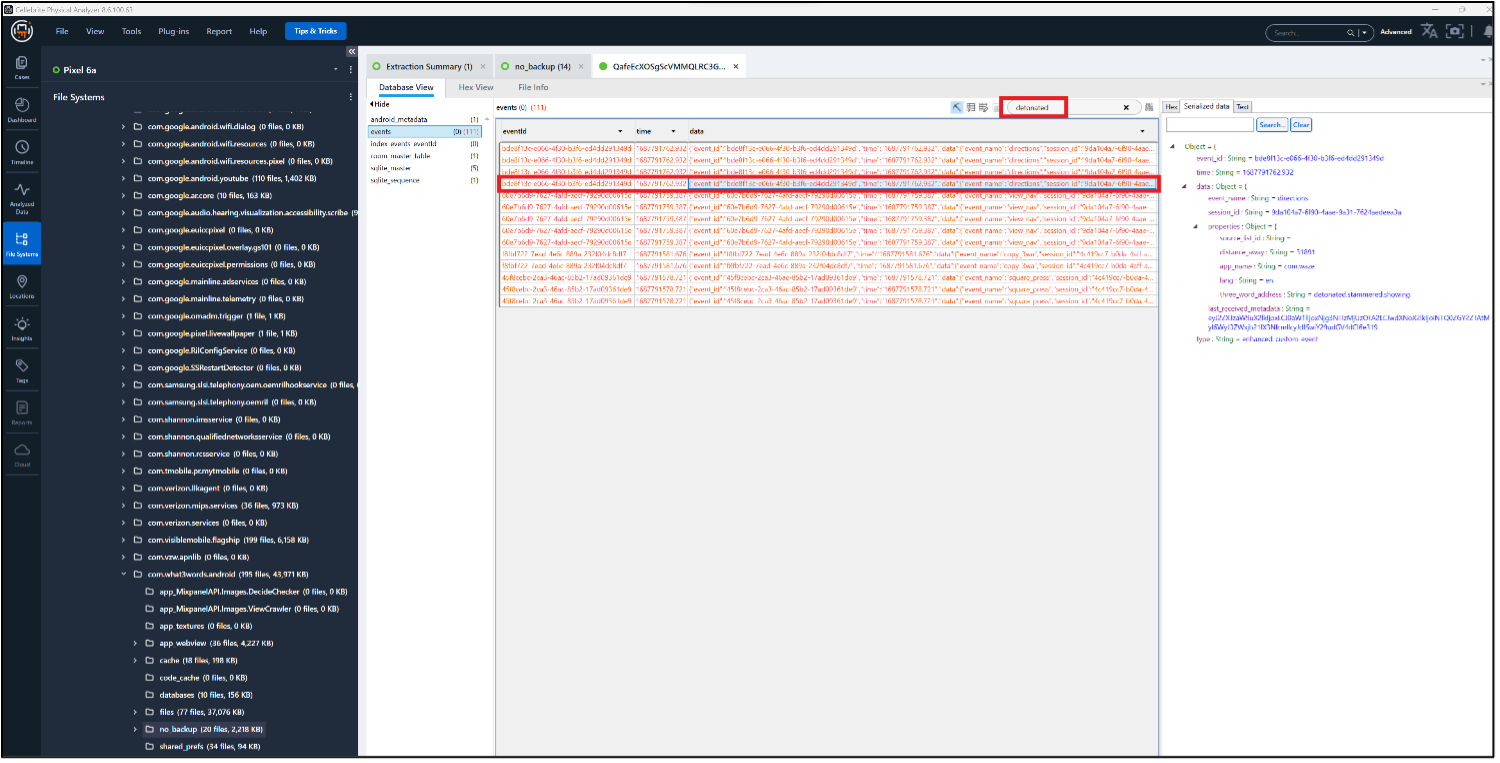
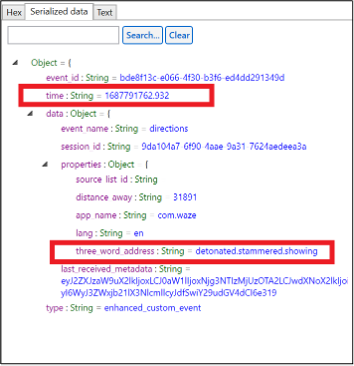
Russell 04 – Signal – Level 1 (10 points)
Was Signal used under Profile 10?
Answer: Yes.
There were multiple ways to find the answer, but we will highlight two here. First was by analyzing the file app_usage_database under the Google Files app /data/user/10/com.google.android.apps.nbu.files/databases/app_usage_database. The table app_usage_stats_table has an entry for com.thoughtcrime.securesms (Signal’s apk name).
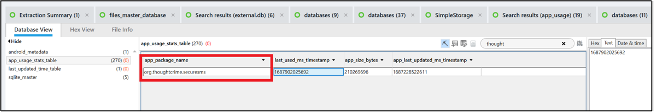
Note that the time listed in the column last_used_ms_timestamp is not the last time Signal was used, which is important in the question Russell 09.
The second way to determine if Signal was used under Profile 10 is by examining the file SimpleStorage, which is a database that, among other things, stores launch times/locations of apps for approximately 24 hours. Josh tweeted (or X’d) about this file several months ago.
Both profiles on Russell’s phone have their own version of SimpleStorage. For Profile 10 it is found in /data/user/10/com.google.android.as/databases/; this file is part of the Android System Intelligence package. The table EchoAppLaunchMetricsEvents contains the relevant data. Initial inspection of this table finds no record of Signal. It had been deleted prior to extraction.
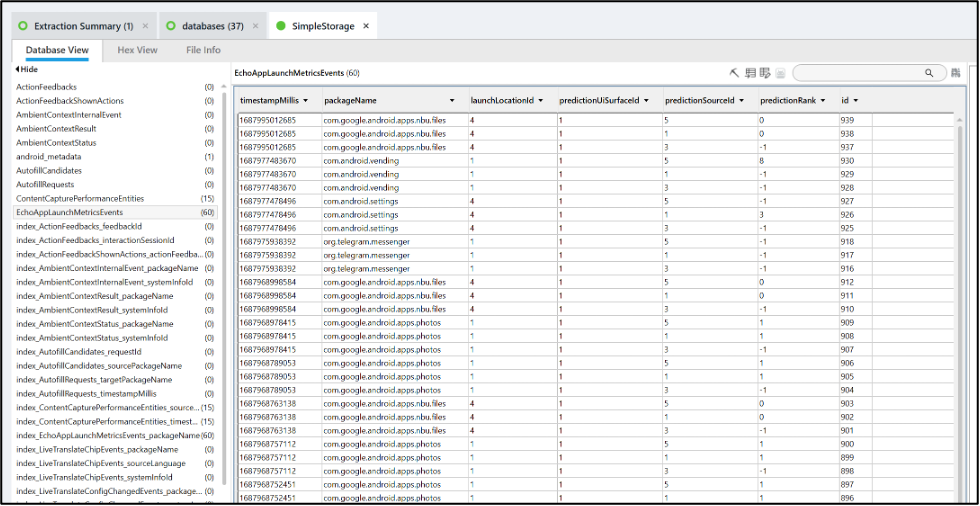
Using PA Ultra’s Include recovered records feature (pickaxe), Signal’s apk name appears in recovered records.
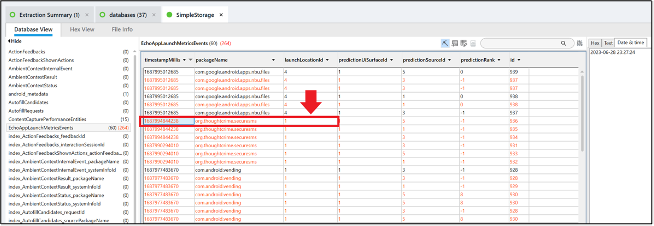
Note the timestamp because you will see it again on Russell 09.
Russell 05 – Phone – Level 2 (30 points)
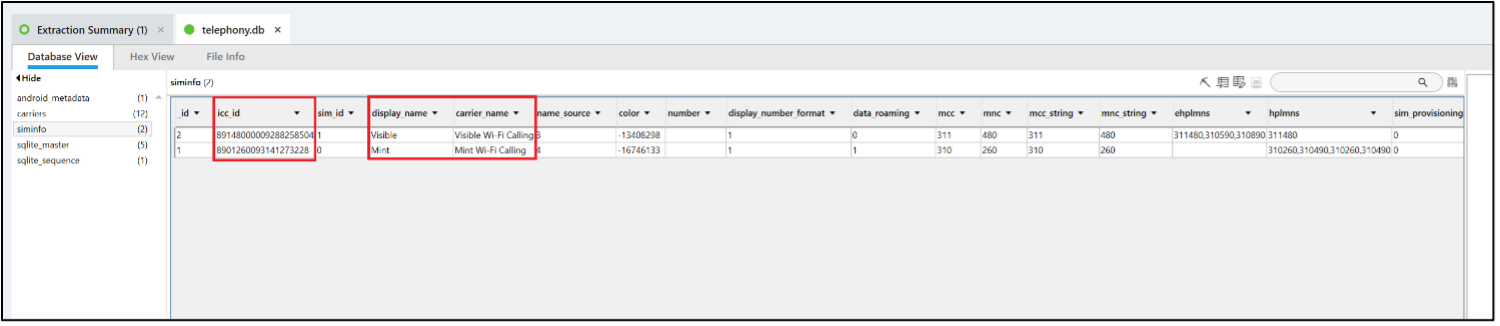
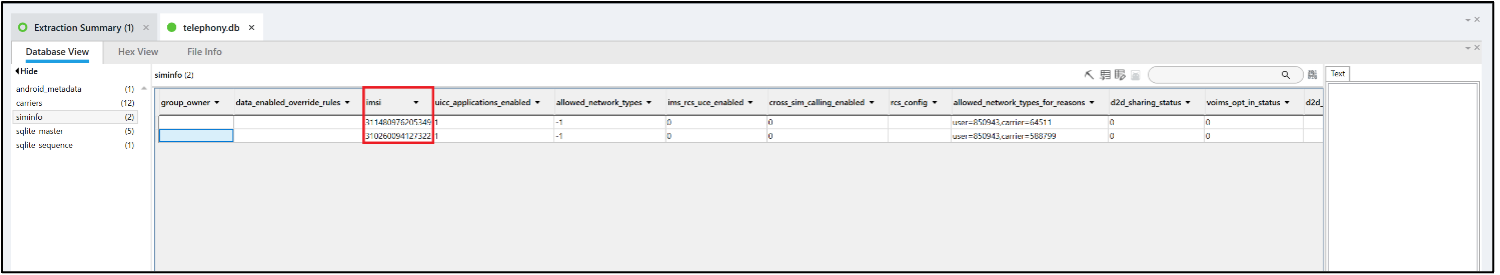
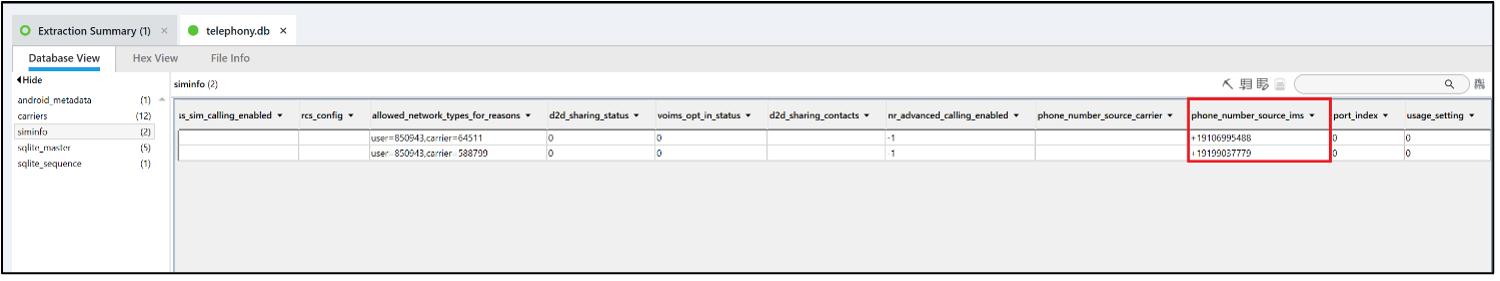
Associate the phone number(s) of the phone with the correct ICCID, IMSI, and Carrier.
Answer: +19106995488, +19199037779
|
Phone |
ICCID |
IMSI |
Carrier |
|
+19106995488 |
89148000009288258504 |
311480976205349 |
Visible |
|
+19199037779 |
8901260093141273228 |
310260094127322 |
Mint |
PA does not associate phone numbers with ICCIDs, IMSIs, or carriers in this fashion, but it is easy to do. The table siminfo in the database /data/user_de/0/com.android.providers.telephony/databases/telephony.db contains this data and associates these items.
Russell 06 – Navigate – Level 2 (30 points)
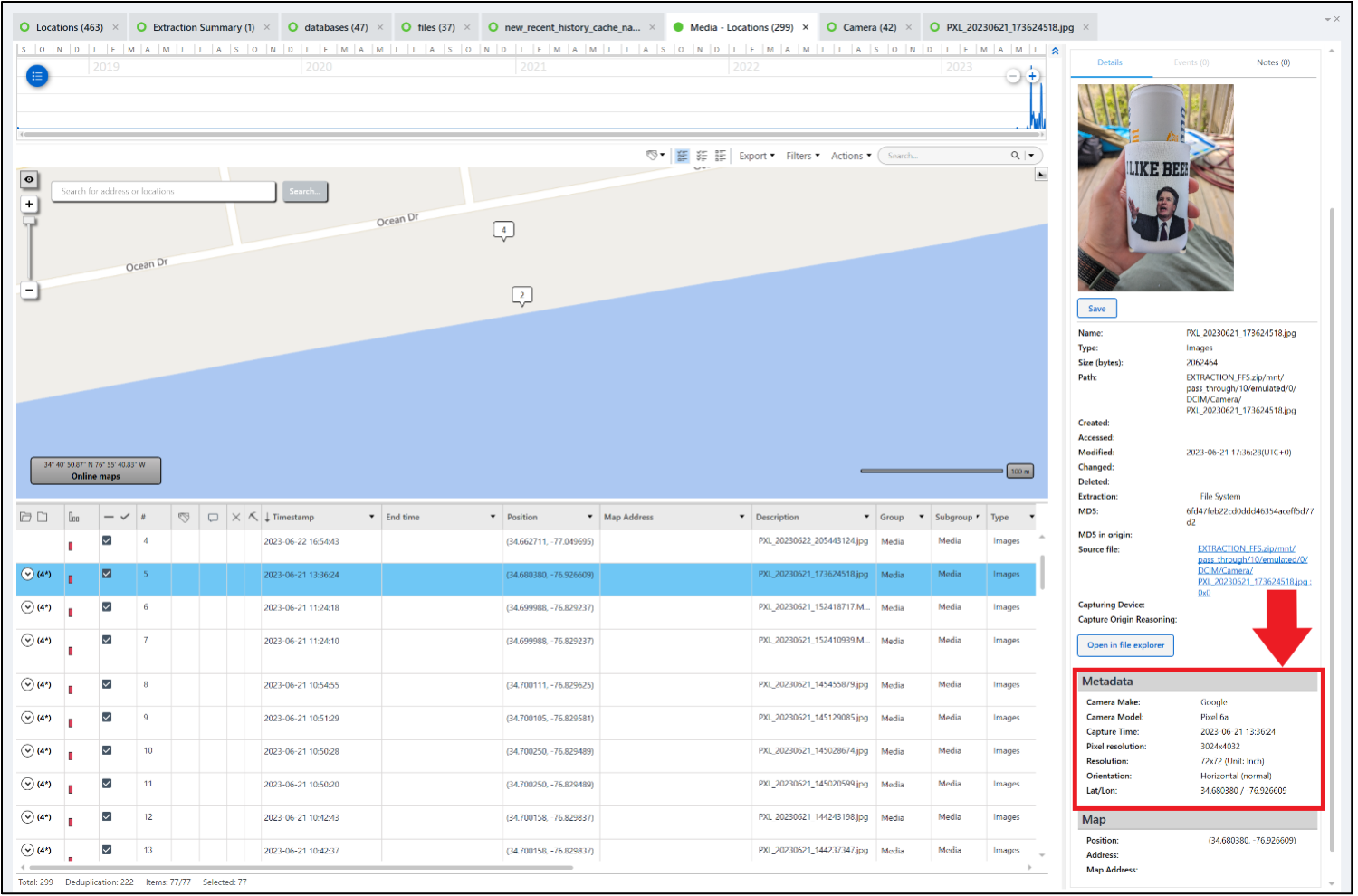
Russell went on a coastal vacation. Where did he stay?
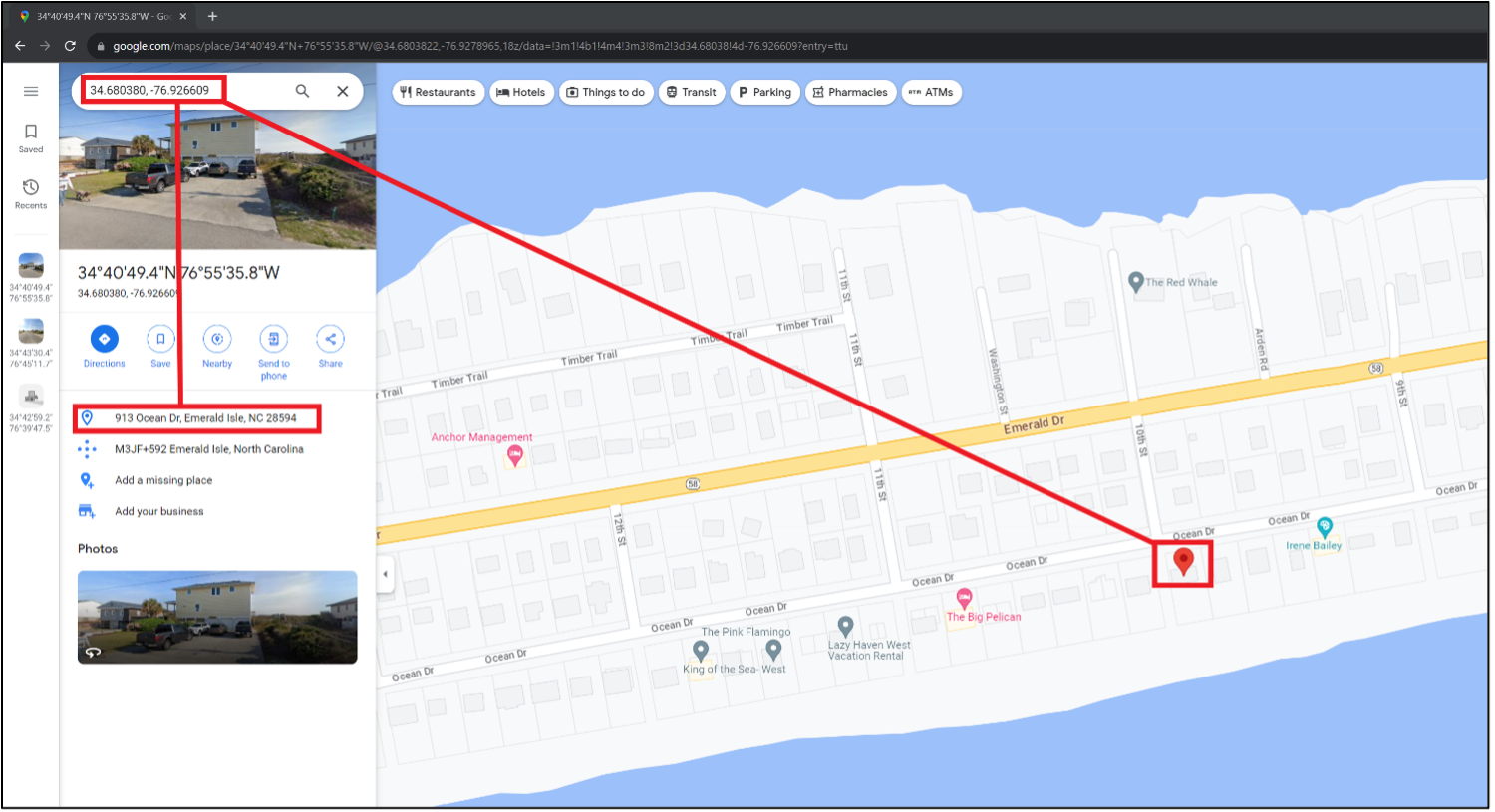
Answer: 913 Ocean Drive, Emerald Isle, NC 28594
This address is a beach-front house and getting the location can be multiple ways. One way involves using metadata from a picture taken on the back deck of the house. The GPS coordinates associated with the picture are for the house.
Another way to get the location was related to a webinar our very own Jean-Philippe Noat and Ian Whiffin did earlier this year. The file new_recent_history_cache_navigated.cs contains Google Maps navigation history and can be found in /data/data/com.google.android.apps.maps/files/ for Profile 0. The file contains, among other things, navigation history. The file is a protobuf so Mushy is used for a quick win.
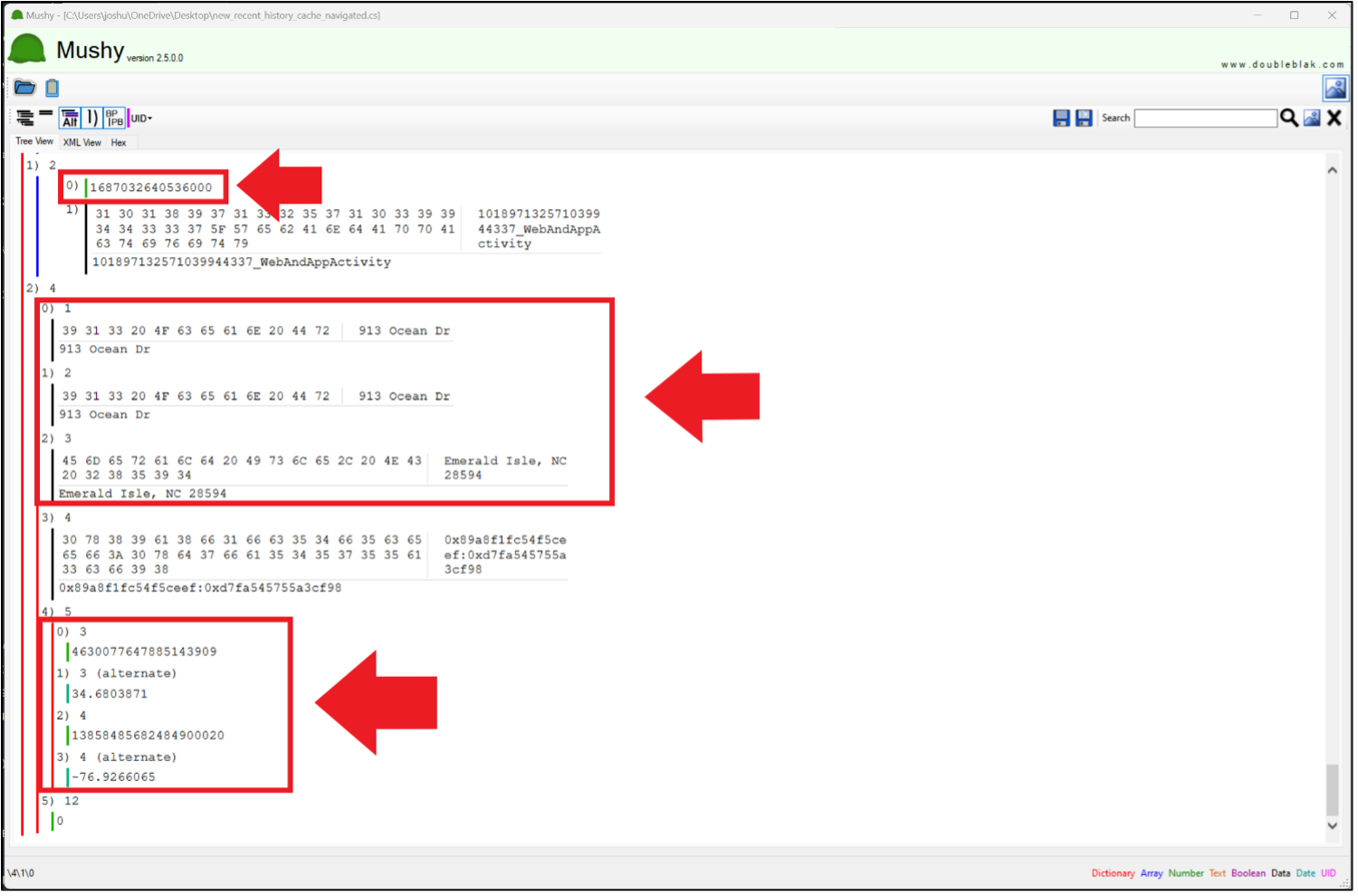
Note the timestamp because you will need it for Russell 11.
Russell 07 – Meetup – Level 3 (50 points)
Sharon, Abe, and Russell all met in-person. When & where (name and location)?
Answer: Cloud 9 Rooftop Bar, Wilmington NC, 2023-06-05-23:03
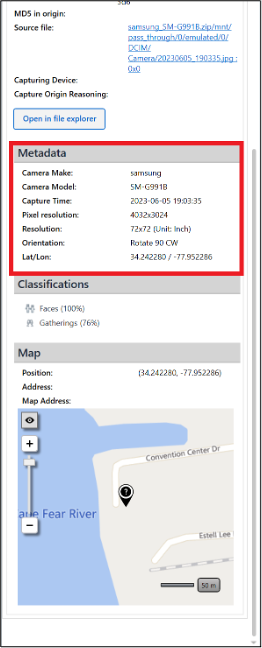
This requires data from Sharon, Abe, and Russell’s phones. For Russell, the picture PXL_20230605_230852752.jpg depicts a view of the Cape Fear River and Cape Fear Memorial Bridge in Wilmington NC. The metadata for the photo includes GPS coordinates.
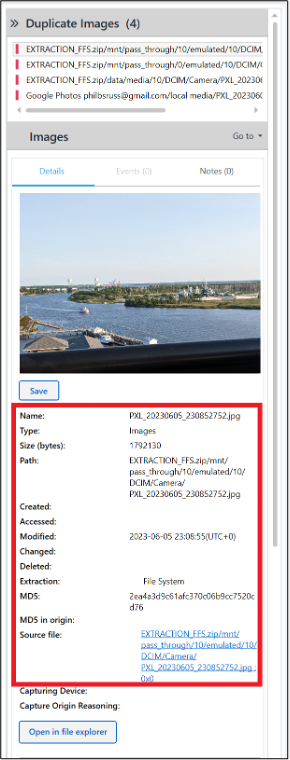
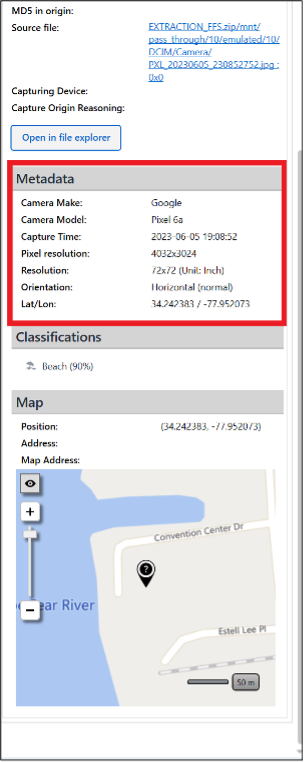
The date and time align with a picture on Abe’s phone (IMG_1105.HEIC), which also happens to depict the same view as the picture from the Pixel. Its metadata also contains GPS coordinates which places Abe at the same location.
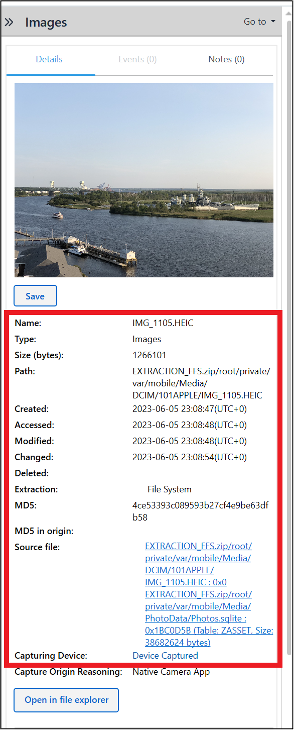
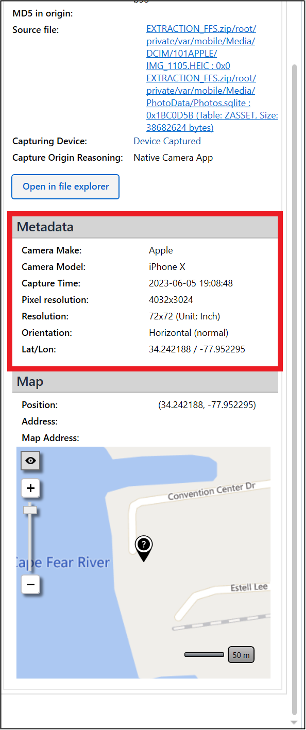
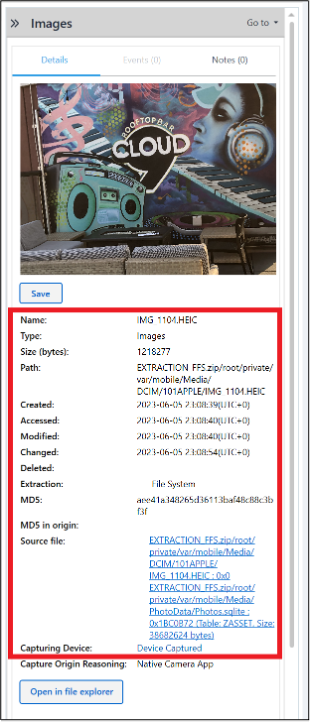
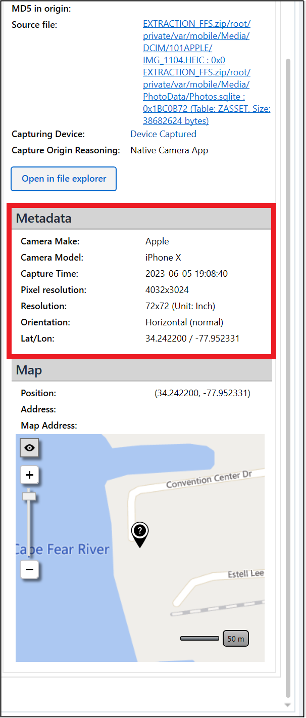
Just prior to IMG_1105.HEIC, IMG_1104.HEIC was taken on Abe’s phone; it has the name of the location: Cloud 9 Rooftop Bar.
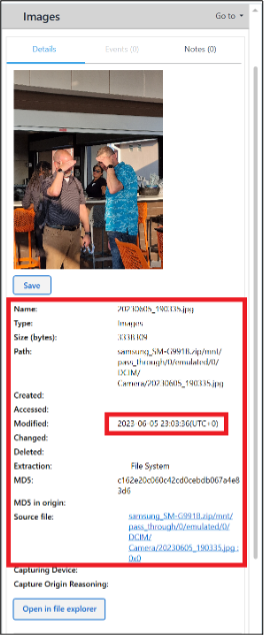
On Sharon’s phone, the pictures 20230605_190334.jpg and 20230605_190335.jpg are taken one second apart and show Abe (Ronen) and Russell (Josh). Also note the location metadata associated with the pictures.
Mjolnir makes an appearance on Russell’s phone. Which app did it come from?
Answer: Reddit or com.reddit.frontpage
Mjolnir (Thor’s Hammer) appears in the picture file Screenshot_20230622-093735.png.
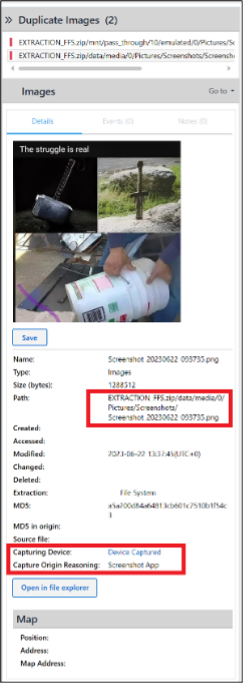
PA reports two things of interest. First, the file path /data/media/0/Pictures/Screenshots, which is certainly indicative. Second, and this only applies if you used PA Ultra, information related to the new Media Origin feature:
Capturing Device: Device Captured
Capture Origin Reasoning: Screenshot App
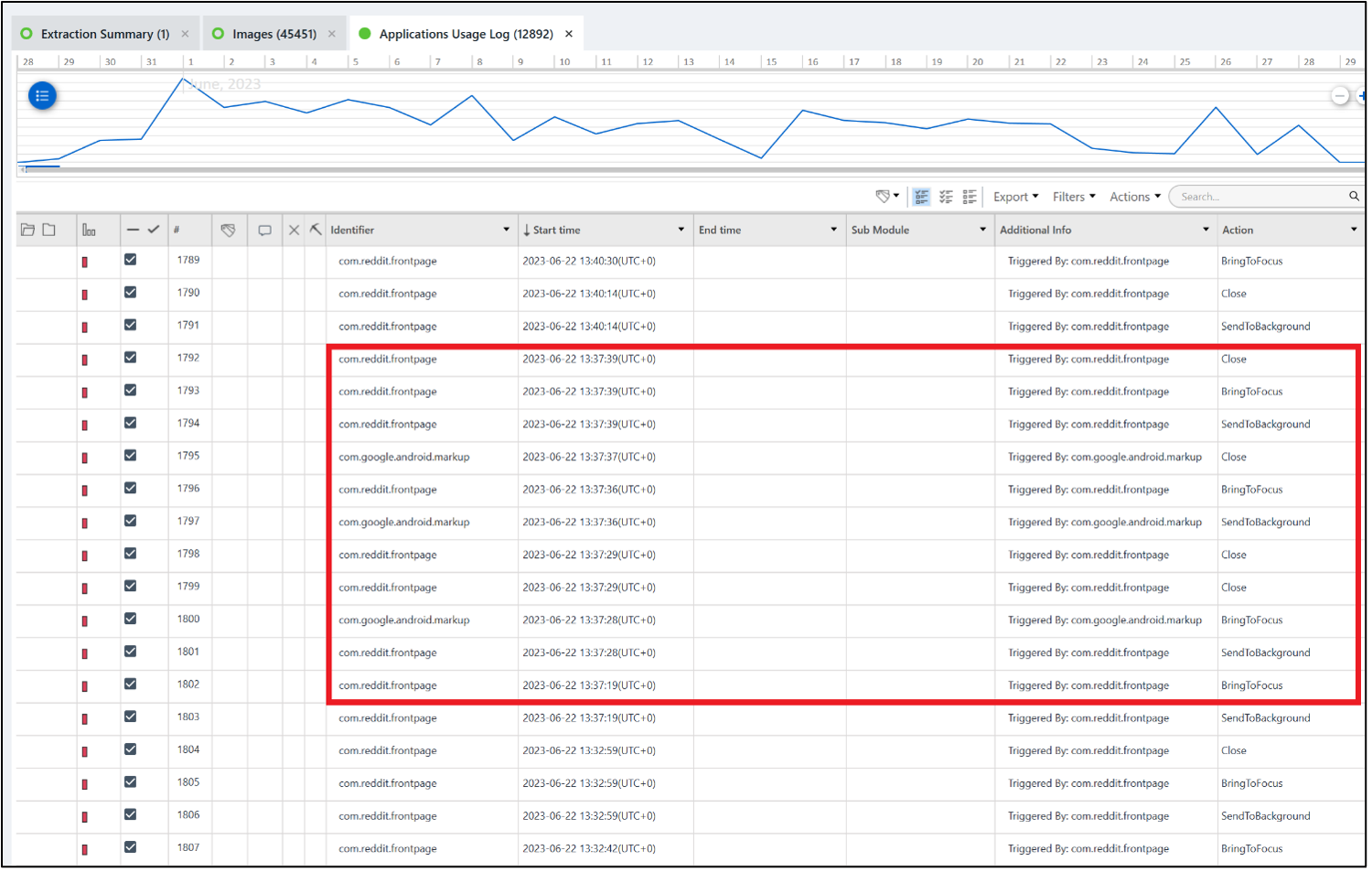
These two data points, collectively, indicate a high likelihood this picture is a screenshot. But from where? Checking Application Usage around the time of the picture creation finds that com.google.android.markup and com.reddit.frontpage were being used. Markup is an internal Android apk, but com.reddit.frontpage (Reddit) is not.
Russell 09 – Signal – Level 2 (30 points)
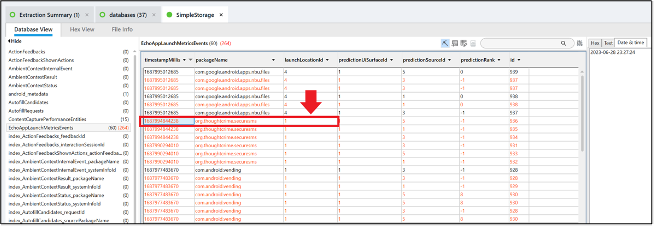
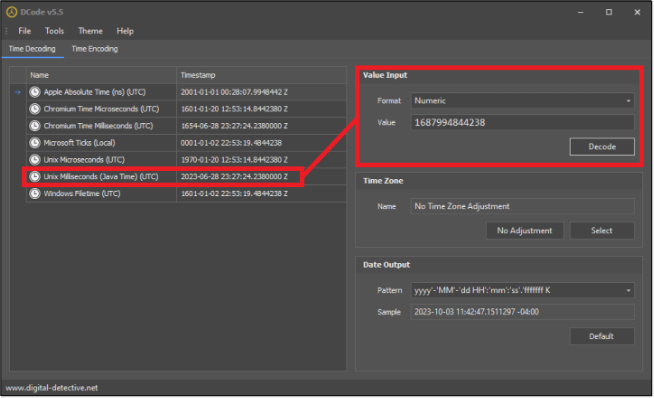
When was the last time Signal was launched (opened) under Profile 10?
Answer: 2023-06-28 23:27:24
If you answered Russell 04 correctly, this question would have been available to you, so refer to the solution for that question on how to get to the file SimpleStorage and why it is important. Converting the Unix Epoch timestamp in the column timestampMillis associated with com.thoughtcrime.securesms gets the answer.
Russell 10 – Big MAC – Level 3 (50 points)
Russell liked to cover his tracks while traveling and connecting to WiFi. What MAC address was used on 2023-06-07 at approximately 23:27 UTC?
Answer: b2:6a:79:dc:9f:08
On 2023-06-07 at approximately 23:27:23 UTC a screenshot was created on Russell’s phone that shows he and Abe were together. It is the same screen shot from the question Russell 01.
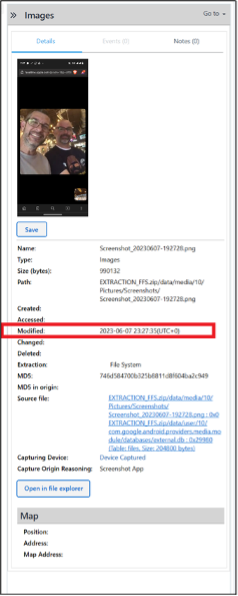
You will not find any location data on Russell’s phone from around this time. So, you needed to examine Abe’s phone. In PA Ultra, you can use the Locations model to find where Abe was at the time; you can filter by the timestamp column.
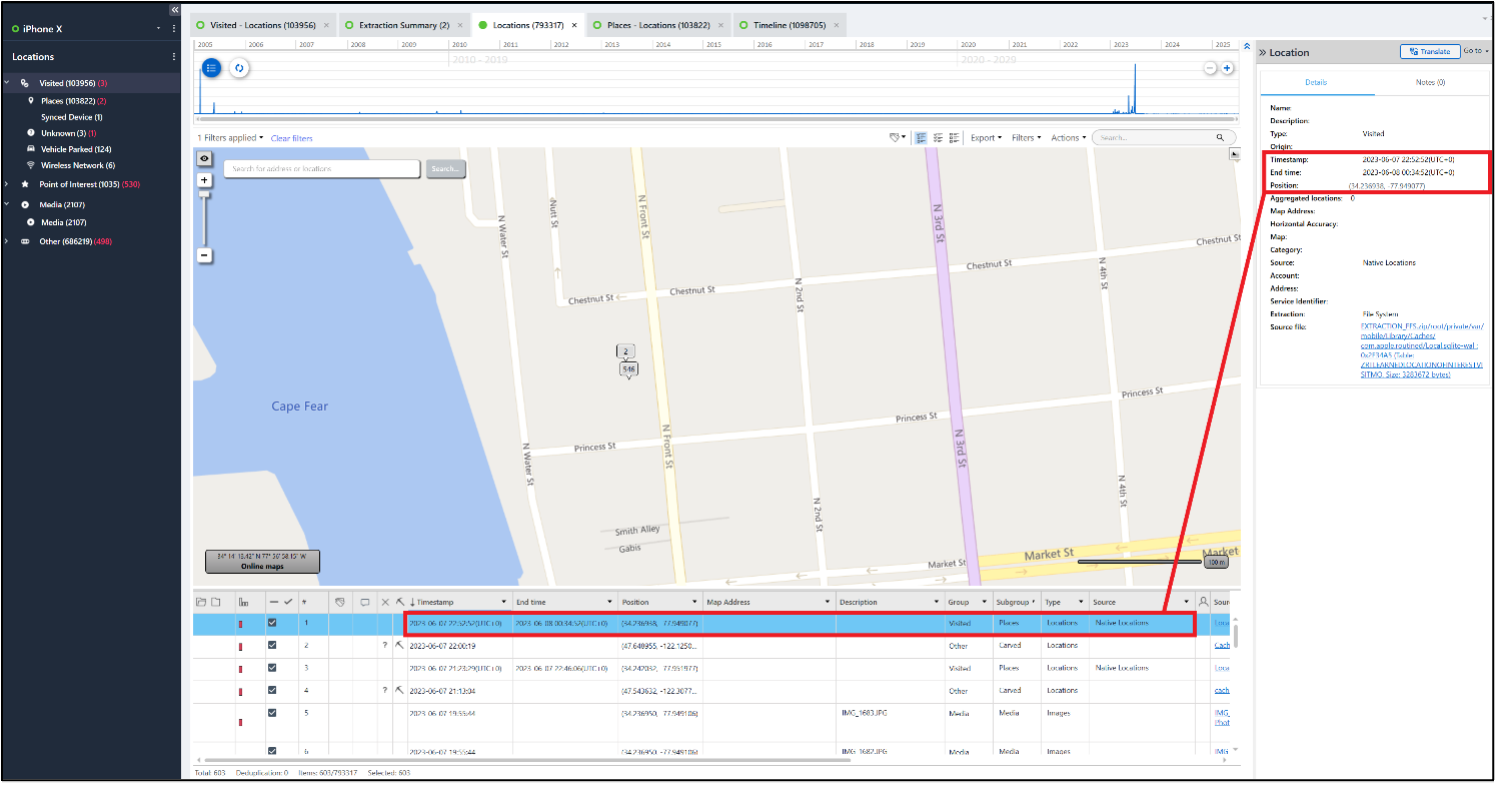
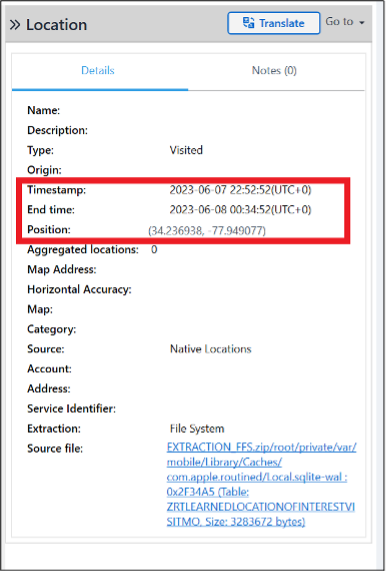
Plotting the latitude and longitude find that Abe and Russell were at the Shuckin’ Shack Oyster Bar in Wilmington, NC.
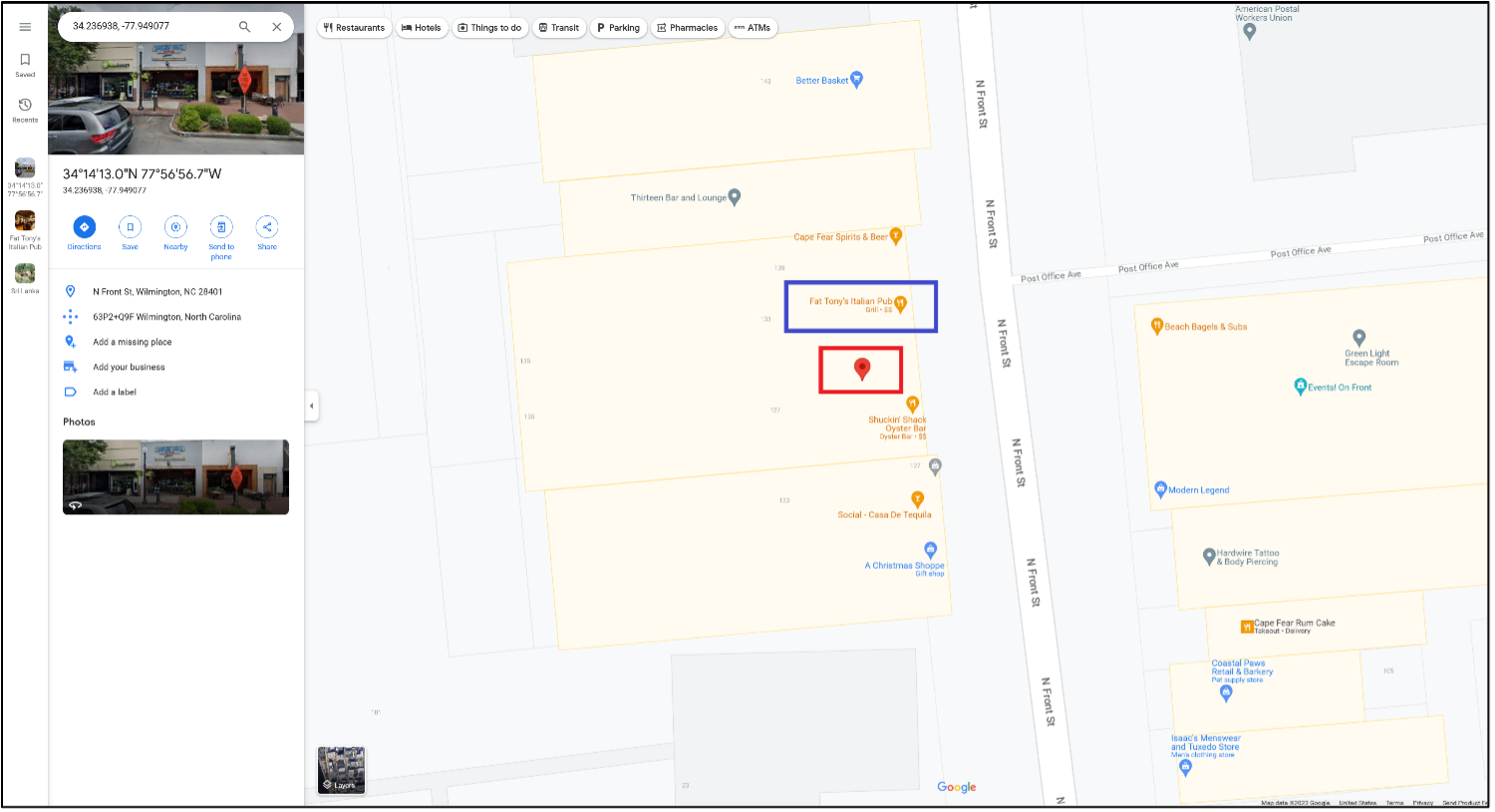
Above, we can see Abe’s location in the red box, which was Shuckin’ Shack Oyster Bar. Right next to that restaurant is Fat Tony’s Italian Pub, which is one of the SSIDs seen in the file WiFiConfigStore.xml, which is located at /data/misc/apexdata/com.android.wifi/. Looking in the file finds the SSID and associated randomized MAC address used to connect to the SSID.

While the randomized MAC address is highlighted, and is the correct answer, you needed to confirm the MAC randomization setting by examining the value of the XML tag MacRandomizationSetting. In Android, MAC randomization can be set on a per-network basis.
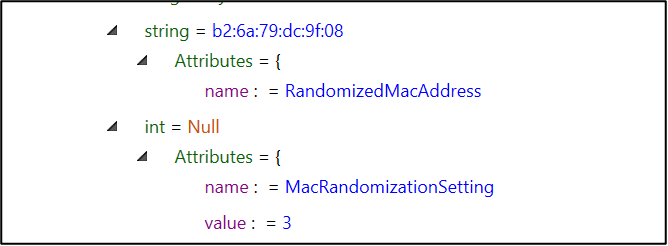
The setting has a value of “3” which means MAC randomization was enabled for the SSID “Fat Tony’s Italian Pub.” If the value had been “0” that would have meant MAC randomization was disabled for that specific network.
Russell 11 – Navigate– Level 3 (50 points)
Russell went on a coastal vacation. What time did Russell first navigate to his coastal vacation house?
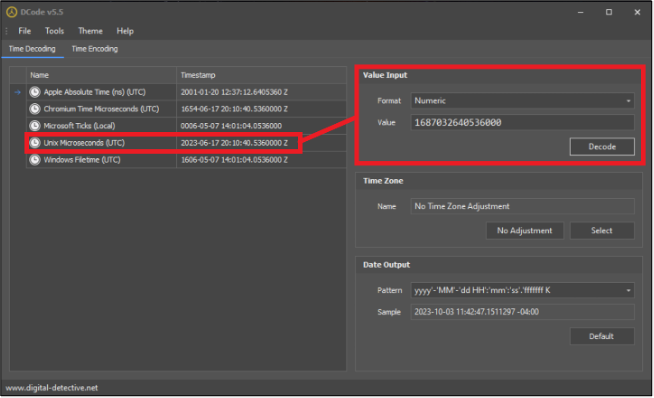
Answer: 2023-06-17 20:10:40
You needed to answer Russell 06 correctly to see this question.In the solution to that question, we discussed the file new_recent_history_cache_navigated.cs, which contained Google Maps navigation history and can be found in /data/data/com.google.android.apps.maps/files/ for Profile 0. The file contains, among other things, navigation history, including the timestamp for the navigation. The file is a protobuf so we used Mushy.
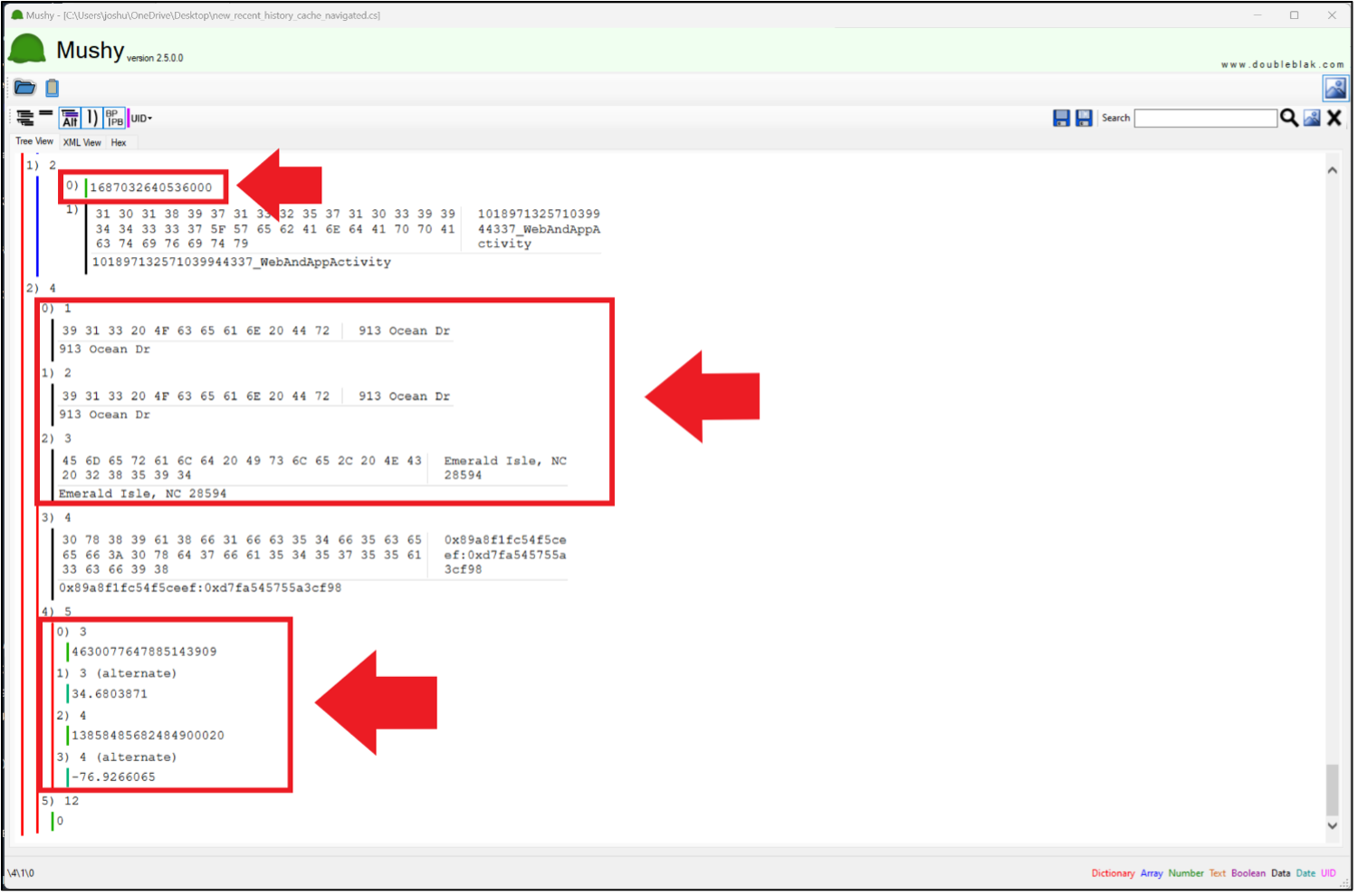
The timestamp highlighted here (top box) is the time at which the navigation started.
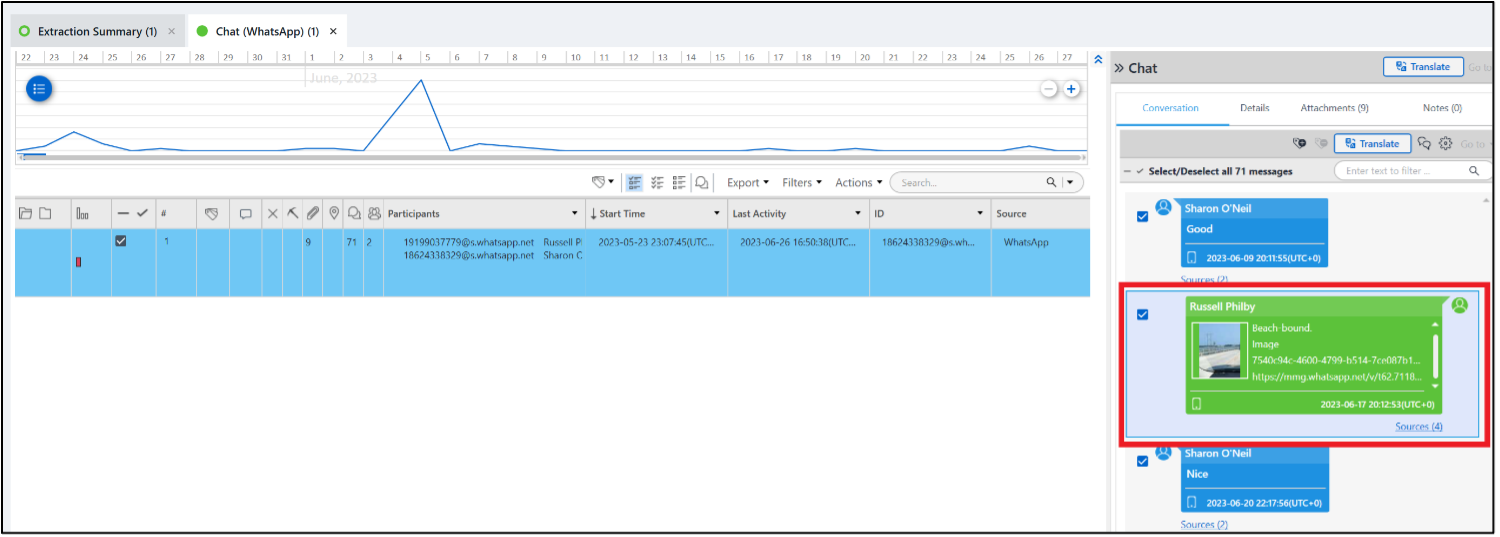
To help with the time, there is a WhatsApp message that Russell sent to Sharon on 2023-06-17 at 20:12:53 that says “Beach-bound.”
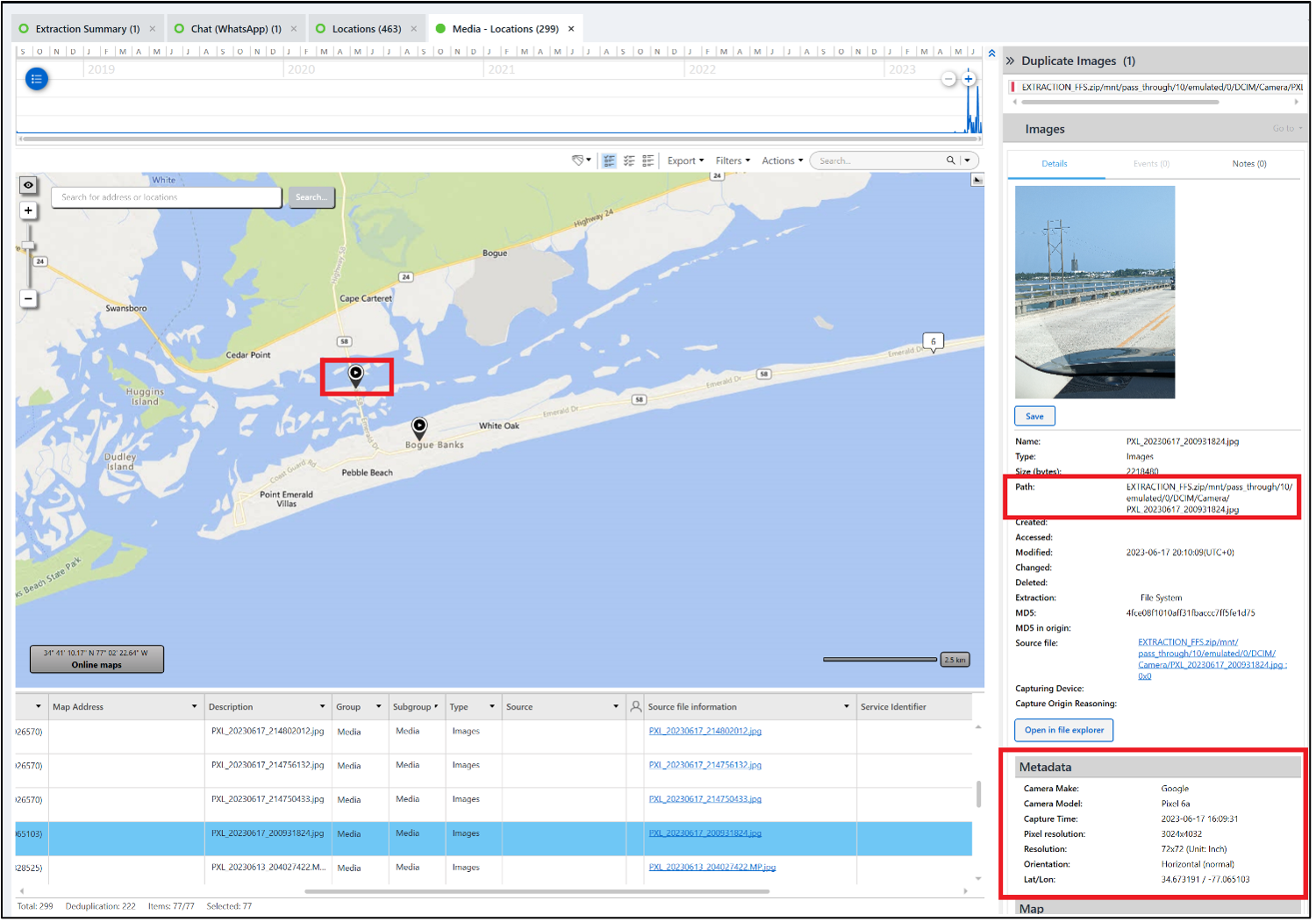
There is an attached picture that appears to have been taken from within a car on a bridge. That same picture is PXL_20230617_200921824.jpg. The picture has a set of GPS coordinates that puts it on the Emerald Isle Causeway (bridge).
Russell 12 – Location – Level 3 (100 points)
Russell called an audible and sent Abe a new location. What was the location?
Answer: Resurrection Cemetery or Our Lady of Heaven Chapel Mausoleum
This one is tough, but there is a small hint in the question itself (“called an audible”). Calling an audible is a phrase used in American football that means a play (the plan) has been changed, and Russell indicates that in his message to Abe when he sent him the new location. If you answered question Russell 6 correctly, you would know that Russell was using what3words to send location information, which is what he used here. Additionally, if you answered questions Russell 04 and 09 correctly, you would already know which file contains the answer to this question.
The database file SimpleStorage (/data/user/10/com.google.android.as/databases/ – for Profile 10) has a table called PecanConversationMessage that, at first look in PA, appears to be empty (some tools will show this table as populated).
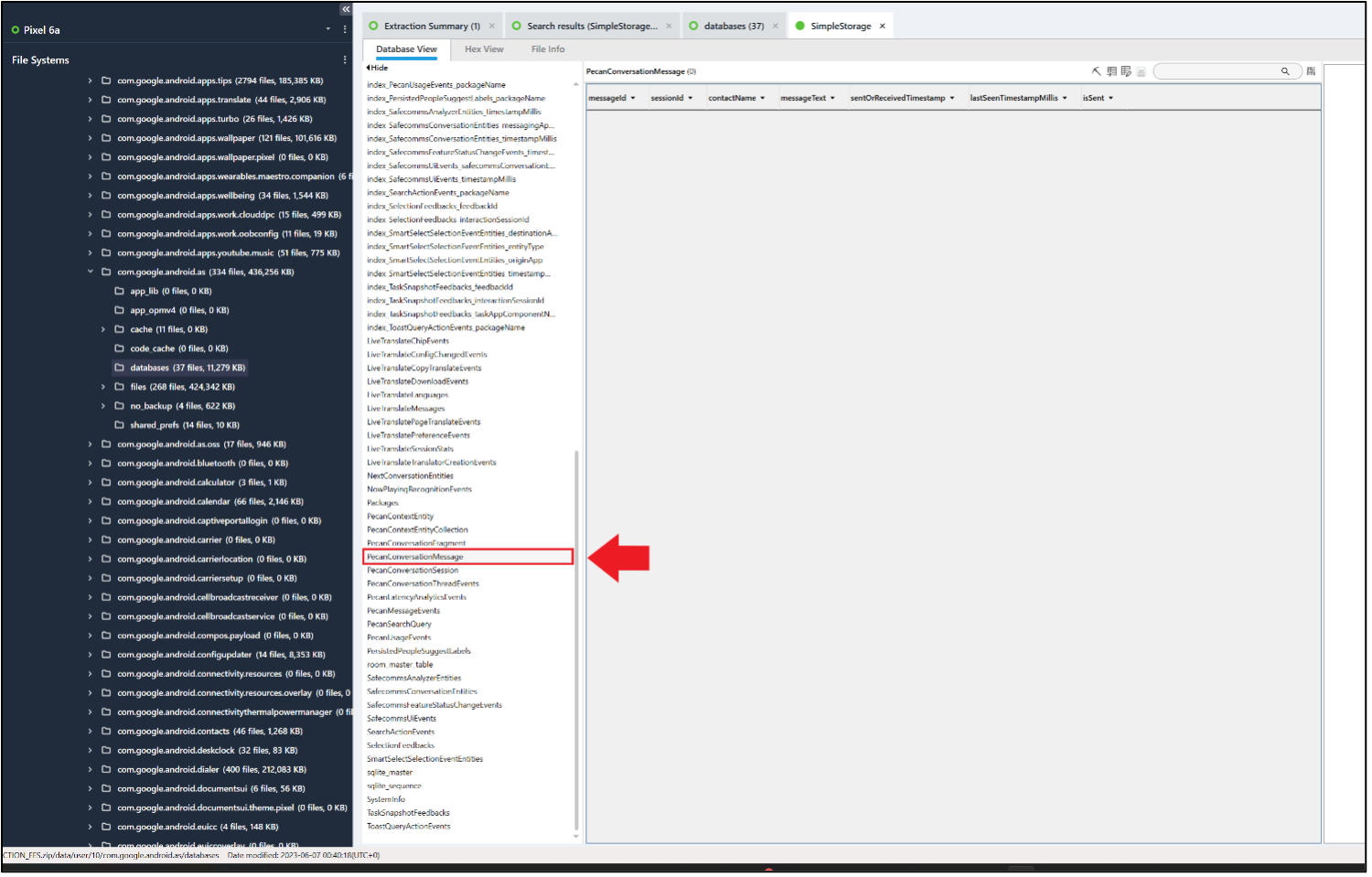
As before, using the pickaxe feature reveals multiple deleted entries.
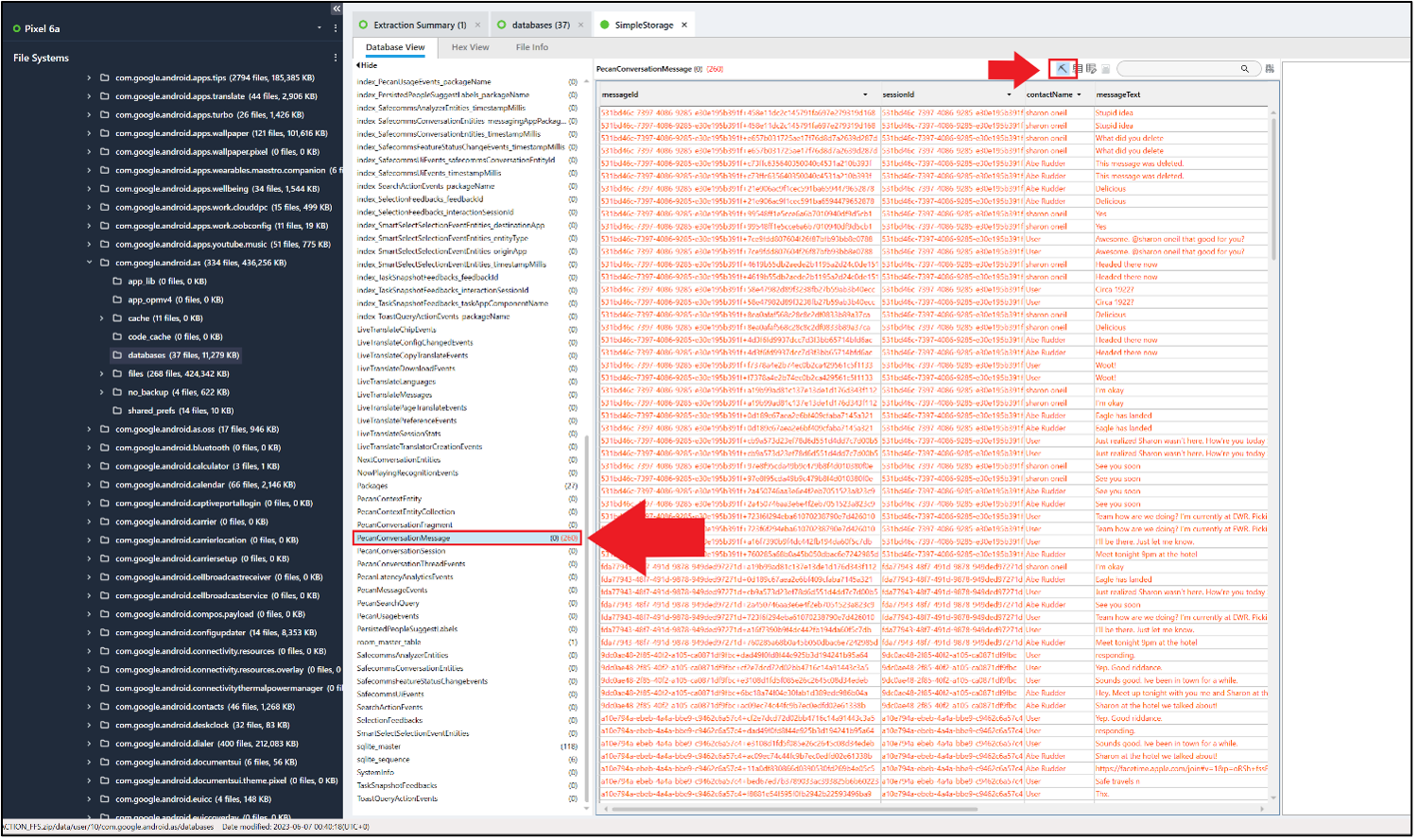
This table is logging conversation content from various apps; you can determine which app by taking the value in the column sessionId and finding the corresponding package name in the table packageName (in this case it is com.thoughtcrime.securesms – Signal). Additionally, you can see which user sent the message in the column contactName.
We know there was a change, so searching for the word “change” in PecanConversationMessage finds just three entries, which are all the same.
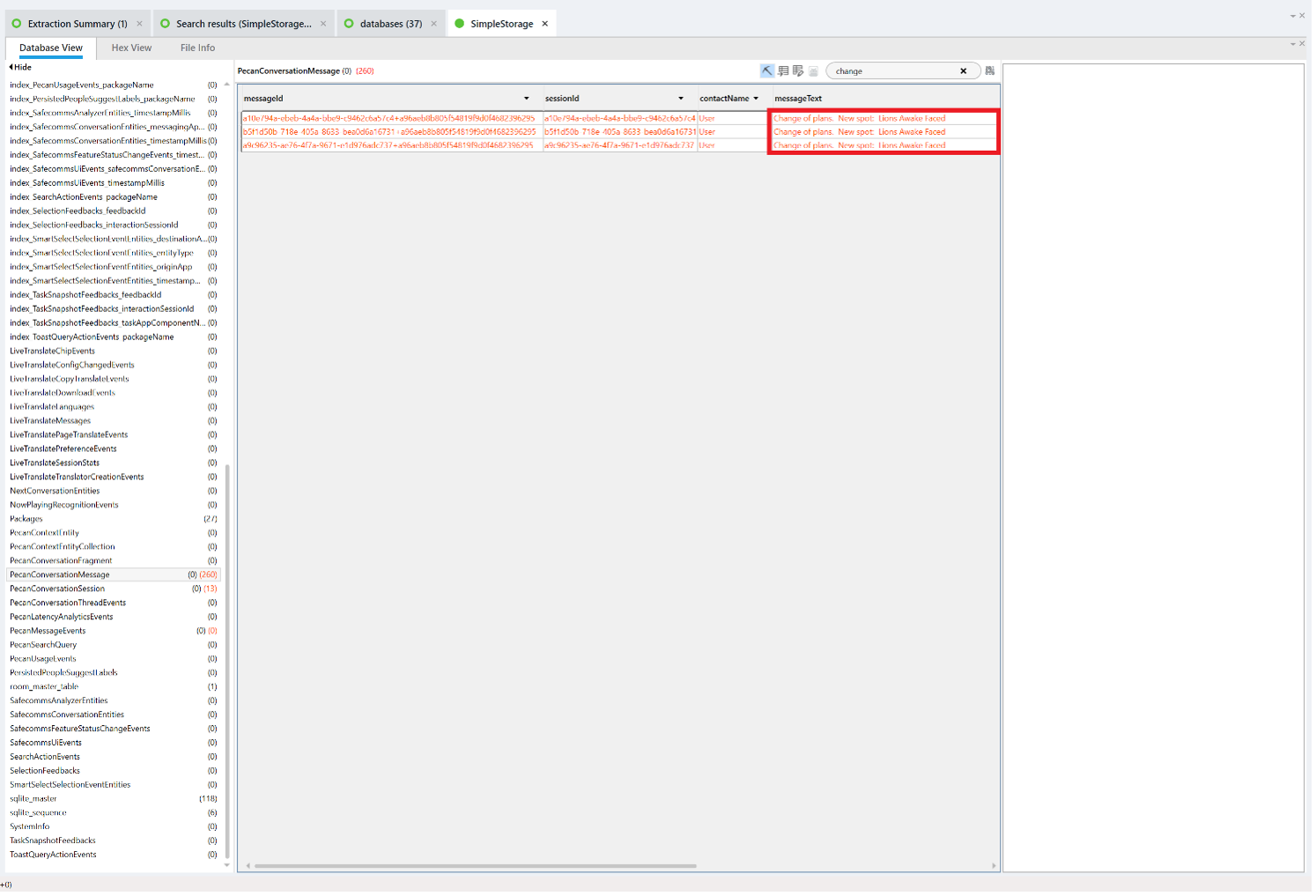
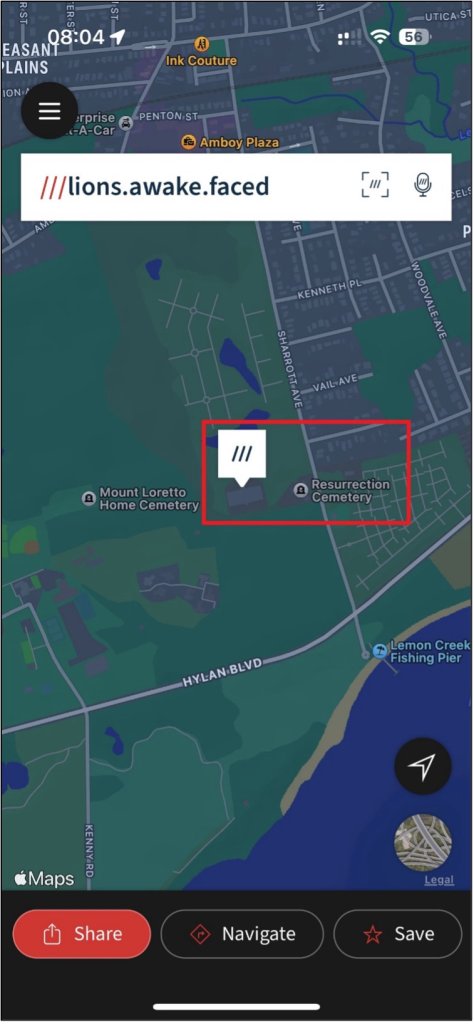
The message “Change of plans. New spot: “Lions Awake Faced”” refers to a location in what3words and is not found anywhere else in the extraction. Plotting that location in the app finds that it is located in the Resurrection Cemetery/ Our Lady of Heaven Chapel Mausoleum.
We hope you enjoyed this CTF. Please feel free to provide feedback on your experience and feedback on PA Ultra to ctf@cellebrite.com. Stay tuned for the next blog and a webinar where we go over the hardest questions to solve and show you how we did it and why we created it.