
Cellebrite’s CTF 2023 Recap: Answers on Abe’s iPhone

We would like to thank everyone who participated in the Capture the Flag event. There were many late evenings and lots of hard work by many people involved. This is Cellebrite’s way of giving back to the community and providing resources to keep learning!
We want to provide a walkthrough on how we arrived at the answers. There may be situations where we show a method of deriving the answer which may differ from the method you used. This is the beauty of forensics—the paths we take may differ, yet the results are the same.
The Backstory/Scenario:
Terror attacks were planned for Southport, NC in June of 2023. Russell, the primary suspect, lives locally to that area and seems to have been introduced to Abe via Sharon. Russell and Sharon go way back, and she seems to be the linchpin who tied Abe to Russell. So, who is Abe? How is he involved with Felix? Why would Felix be feeding a US person with information on nuclear power plants and weapons? We intend to leave this scenario open-ended but wanted to give you some backstory.
Note: Most screenshots are from PA Ultra, so you may see a slight variation from what you are used to viewing with PA 7.
Abe’s iPhone Questions:
Abe 01 – iCloud – Level 1 (10 points)
Abe used a unique email address for his iCloud account. What is that email address?
Answer: aberudder@icloud.com
The extraction summary screen in PA Ultra will show this information when you select the Data Details View.
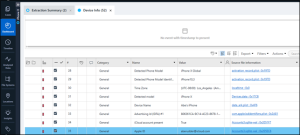
Following the source file can validate the results, which are the same by going to EXTRACTION_FFS.zip/root/private/var/mobile/Library/Accounts/Accounts3.sqlite-wal.
Abe 02 – Comm App – Level 1 (10 points)
Abe used different types of communication channels, through different applications.
What communication application was used the most?
Answer: Telegram
The easiest way to answer this is to look at the Top 5 messaging apps in the Extraction Summary Dashboard View in PA Ultra.
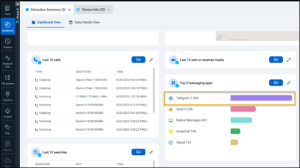
Abe 03 – Wallet – Level 1 (10 points)
A payment card was used on that device’s Wallet. What are the last 4 digits of that card?
Answer: 7438
In PA Ultra, simply go to Analyzed Data and then Finance & Purchase. Under Credit Cards you will find the answer.
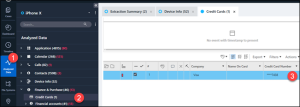
Abe 04 – iCloud Backup – Level 1 (10 points)
Abe’s phone was setup using iCloudBackup method. What is the Date & Time for that (UTC+0 time)?
Answer: 02/20/2023 01:43:14
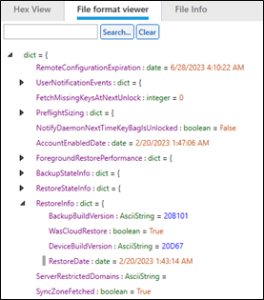
The Device Info tab in PA Ultra parses the last restore from backup.
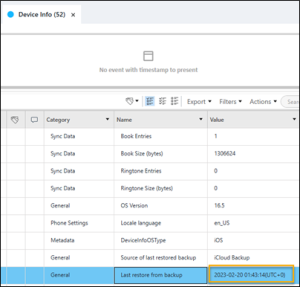
This information can also be found in EXTRACTION_FFS.zip/root/private/var/root/Library/Preferences/com.apple.MobileBackup.plist. The RestoreDate shows the timestamp in this plist.
Abe 05 – Tracking – Level 1 (10 points)
Abe was suspicious about being tracked. After searching the rental vehicle he was using while in NJ, he found a device attached to his vehicle, what was the make/model (need to refine)?
Answer: Geotab go9 lte or Geotab go9
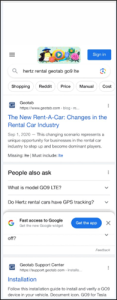
Think about the easiest way to search for something an iPhone. Often this will be Safari. Within PA Ultra go to Analyzed Data and then Search & Web and Searched Items. Under Safari, you will find search hits related to a Hertz rental car and the device, which is the answer. Both are accepted.
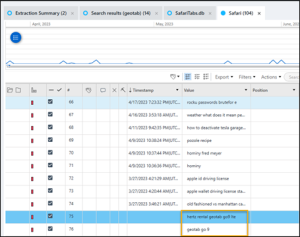
The source file for this answer can be found in EXTRACTION_FFS.zip/root/private/var/mobile/Library/Safari/SafariTabs.db.
There’s a screenshot of this search as well. This can be found if you go into the media images and filter on Path for “safari.” You will find the screenshot below, which can also be found in this path EXTRACTION_FFS.zip/root/private/var/mobile/Containers/Data/Application/F3458CE0-DDB8-4E78-8A26-13F93CC5A920/Library/Safari/Thumbnails/77A3C03A-FFEF-400D-9994-015E93BEAD69-v2.ktx
Abe 06 – Steps – Level 2 (30 points)
Abe was not really active on 6/24/2023 local time. How many steps were recorded?
Answer: 755
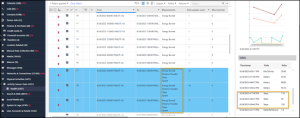
In PA Ultra, go to Analyzed Data and then Activity Sensor Data and Health. You can filter on date under the From column and then look for steps in the Measurements. Add all the steps together as shown here: (119 + 95 + 129) + (65 + 36 + 29 + 65) + (21 +108 +88).
This information can also be manually found in the following file EXTRACTION_FFS.zip/root/private/var/mobile/Library/Health/healthdb_secure.sqlite.
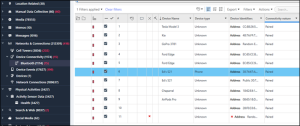
Abe 07 – Bluetooth – Level 2 (30 points)
How many unique Bluetooth connections were paired?
Answer: 10
Under Analyzed Data > Networks & Connections > Device Connectivity > Bluetooth you will find several results. Filter the results on Paired under the column Connectivity nature. The answer is 10, not 11 since there are 2 which are the same (Ed’s S21).
To manually answer this, 2 connections can be found in EXTRACTION_FFS.zip/root/private/var/containers/Shared/SystemGroup/2CF38A4C-FE38-40D1-85C2-C478DC223554/Library/Database/com.apple.MobileBluetooth.ledevices.paired.db. One more connection is found in EXTRACTION_FFS.zip/root/private/var/containers/Shared/SystemGroup/2CF38A4C-FE38-40D1-85C2-C478DC223554/Library/Database/com.apple.MobileBluetooth.ledevices.paired.db-wal. Another 8 are found in EXTRACTION_FFS.zip/root/private/var/containers/Shared/SystemGroup/2CF38A4C-FE38-40D1-85C2-C478DC223554/Library/Preferences/com.apple.MobileBluetooth.devices.plist. You must deduplicate the S21 found in the plist and the database.
Abe 08 – App Notification – Level 2 (30 points)
Abe got notified by Harold of a potential arrest, Abe then opened which app?
Answer: Signal
One approach to this question is to search for “Harold” in PA Ultra. From there, search for “arrest in the resulting keyword hits.
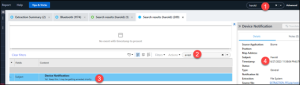
Now we have a timestamp we can filter on. Open the timeline and filter on June 27, 2023. Filter the Source column on Biome and KnowledgeC. We also filtered on the Type column for Device Notifications and AppsUsageLogs. Here you will see Signal was launched right after the text was received. Remember, you may have to adjust your timezone settings to account for Pacific Time.
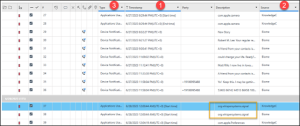
Abe 09 – Parked- Level 2 (30 points)
Abe went to a party at RAIN Event Space. What is the name of the street (just the street name) where he parked his vehicle?
Answer: Water street
There are a couple of ways to approach this question. The easiest utilizes PA Ultra’s Location model. In the Locations model search by “RAIN;” only three results are returned.
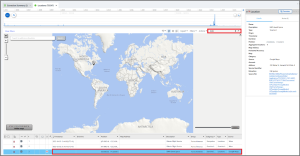
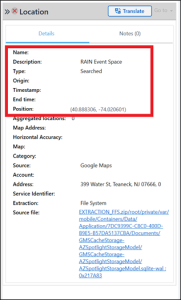
Now that we have the coordinates for the RAIN Event Space, we can search for those coordinates in the Vehicle Parked portion of the Locations model, which returns the answer.
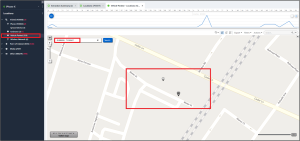
Abe 10 – About – Level 2 (30 points)
What was Abe Rudder’s About bio on Whatsapp?
Answer: World peace
WhatsApp is one of those apps that makes use of the /Shared/AppGroup/ location in iOS. A good resource here is the SANS iOS Third-Party Apps poster, which shows that preferences are stored in the /Shared/AppGroup/ folder in the file group.net.whatsapp.WhatsApp.shared.plist. You can easily navigate to this file by searching for it. There is only one result, which is found in /root/private/var/mobile/Containers/Shared/AppGroup/6FF228A4-E82F-4E85-A27F-159687F96EF3/Library/Preferences/.
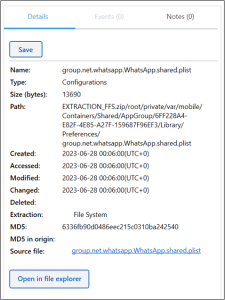
Opening the file in PA and scrolling down to the entry “CurrentStatusText” finds the value “World peace” with an accompanying emoji.
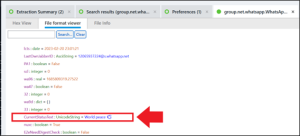
Abe 11 – Permissions – Level 2 (30 points)
Abe is paranoid and not always giving access to everything. One of the apps Abe used on the iPhone received access to Photos however as an “Add Photos Only” permission. What is the name of the app (one word i.e: Starbucks).
Answer: Chrome
Since we are talking iOS permissions, the best location to look is the Transparency, Consent, and Control (TCC) database, or TCC.db. It can be found in /root/private/var/mobile/Library/TCC/.
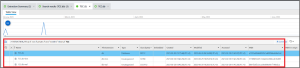
The table of interest here is access. Filtering by any value that contains “photos” narrows the amount of data we need to examine.
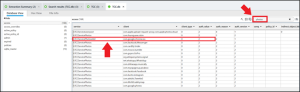
After narrowing the results, there is a single entry associated with the kTCCServicePhotosAdd access permission: com.google.chrome.ios or Chrome.
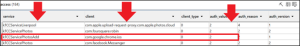
Note the value of 2 in the auth_value column, which indicates Chrome was granted access to that permission.
Abe 12 – Email – Level 3 (50 points)
Abe used a specific method to find/check/share locations via an app. In order to keep privacy up, Abe signed up with a different email address which keeps it isolated to that vendor. What is that email address?
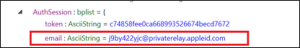
Answer: j9by422yjc@privaterelay.appleid.com
This team really liked using the app What3Words to find and send location information, so we know that is likely candidate. With that in mind there are a couple of ways to approach this question. The first is by using email. Searching for “what3words” returns three (3) email messages from What3Words that contains the email address j9by422yjc@privaterelay.appleid.com. This email address is part of Apple’s Hide My Email feature, which uses anonymized email addresses when signing up for online services.
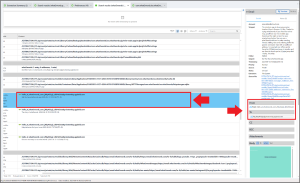
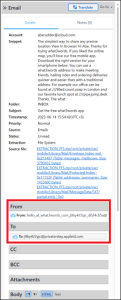
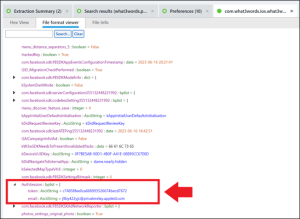
The next option is to examine What3Words’ application data, which is found in /root/private/var/mobile/Containers/Data/Application/016859D5-A1E7-42B4-A070-B743BF01686D/Library/Preferences/. The file com.what3words.ios.what3words.plist contains the email address in use.
Abe 13 – Search- Level 3 (50 points)
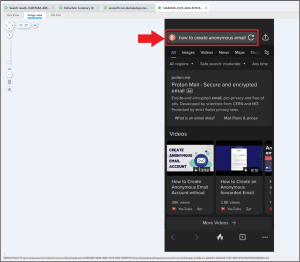
Abe got suspicious when he had to deal with some shady people almost as if a crime was known to be committed and wanted to leave no traces. Abe wanted to create an anonymous email. Where did Abe search for that? (3 words).
Answer: Duck Duck Go
This one may have taken a bit of time. After reviewing all the parsed search history and striking out, it’s time to see what other applications are installed on Abe’s phone that may have allowed him to search. It is here we find Duck Duck Go.
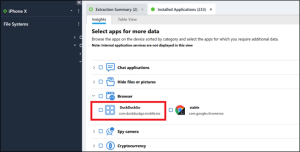
Duck Duck Go is famous for not keeping search history, so we will need to attack this problem from a different angle. Snapshots are a great way to find in-app content that may not be captured by traditional storage mechanisms (e.g., SQLite database, XML file, protobuf, etc.). Searching the extraction for “DuckDuckGo” returns a lot of hits, but they can be narrowed to those that are in /root/private/var/mobile/Containers/Data/Application/. In this location we find data in root/private/var/mobile/Containers/Data/Application/63663962-9D48-4080-9D58-66DE13B95970/. Searching that folder finds the Snapshot directory in ~/Data/Application/63663962-9D48-4080-9D58-66DE13B95970/Library/SplashBoard/.
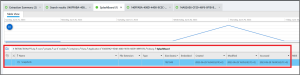
In the folder sceneID:com.duckduckgo.mobile.ios-default has file 14A82AE6-CF29-46F6-8F1B-B52FE4D5A83B@3x.ktx, which contains the answer. The file 140FFABA-408D-4408-9CEC-DD5AC163CC1F@3x.ktx also contains the answer, and it is found in the downscaled folder.
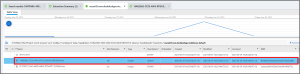
Abe 14 – Navigation- Level 3 (50 points)
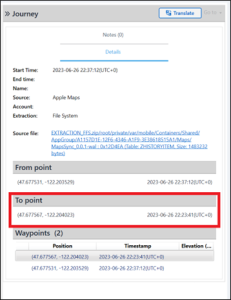
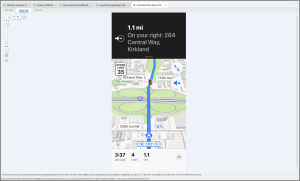
Abe was navigating while driving, on 6/26/23. What was the destination address on the navigation?
Answer: 284 Central Way, Kirkland
This question has a clue for where to start: “navigation.” In PA you can find information about navigation events in Location Related > Journeys. There were only two applications listed, Apple Maps and Google Maps, with Apple Maps having a navigation session on 2023-06-26. Unfortunately, there isn’t an address or location name.
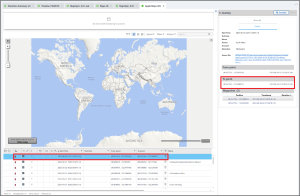
PA’s timeline feature comes in handy here. Using the highlighted timestamp above as an anchor point, we find there is a lot of location-related data during this time, which makes sense if Apple Maps was in use. To help cut down on the noise, filter the column Type to show only Application Usage Log and Images.
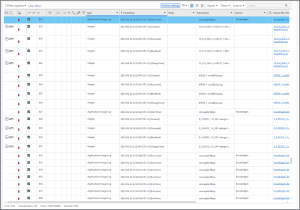
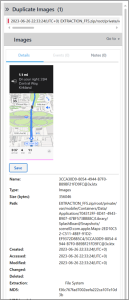
Just beyond this view we find an entry for a snapshot at 22:33:24 which has the answer. It is found in EXTRACTION_FFS.zip/root/private/var/mobile/Containers/Data/Application/704312FF-8D41-4943-B907-47BF573BB88C/Library/SplashBoard/Snapshots/sceneID:com.apple.Maps-2ED10C52-C511-4BEF-91D2-EF9372D8B5C4/.
Abe 15 – Crypto – Level 2 (30 points)
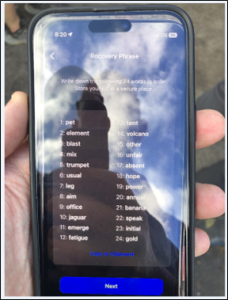
Abe used MOB to send/receive crypto within Signal. Can you find the Recovery Phrase for Signal Mobile Coin wallet? What is it? (24 words)
Answer: pet element blast mix trumpet usual leg aim office jaguar emerge fatigue tent volcano other unfair absent hope power annual banana speak initial gold
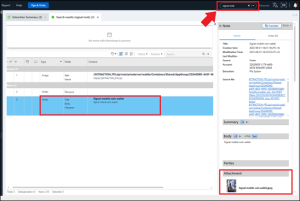
Signal uses MobileCoin (MOB) for in-app payments, which is a cryptocurrency. Part of the setup process involves setting up a recovery phrase. Here, Abe documented the phrase by taking a picture and attaching it to a Note. To find it, search “signal mob” to surface the note. Then open the attached picture.
Abe 16 – Picture – Level 2 (30 points)
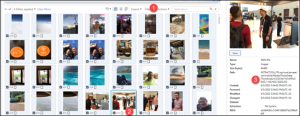
Abe loves taking pictures and videos on the iPhone, the problem is when Abe is trying to look for a picture, he is having hard time finding it therefore he utilizes the Search within the Apple Photos app. If Abe would have looked for a picture of: Myself, Pawel, and Hat he would end up with one photo. Can you name that filename?
Answer: IMG_1100.HEIC
Media classification may be helpful with this question if you are patient enough to dig. We opted to go to Media and Images in Analyzed Data. Then filter on Media Origin and then Device Captured. When you start reviewing the images, you will see a picture of Abe in a hat, with Paul (Pawel) in the background.
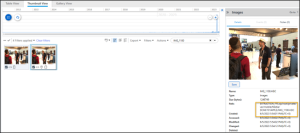
The initial image is the thumbnail, and you need to search for the image to get the correct answer.
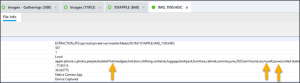
When you open this image and look at File Info you will see all the keywords of the question.
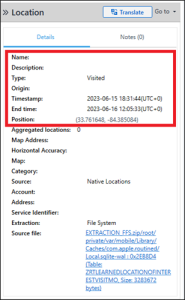
Abe 17 – Location – Level 2 (30 points)
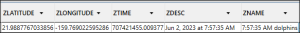
Abe went for some shady meeting on an island but tried to conceal it as a vacation, so he took a boat tour and saw dolphins. He then decided to mark a location with “dolphins”. What was the timestamp for that location [HH:MM:SS] written in UTC time?
Answer: 17:57:35
The answer for this question required a search across the entire extraction using the keyword “dolphins,” which returned just under 350 results. Evaluating the results finds two results that are likely to contain location data:
![]()
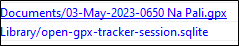
The GPX file is especially of interest here. It is a GPS Exchange Format file that is used to store GPS and ancillary data about locations. Examining the GPX files look like the below image.
And the sqlite file has the following entry in the ZCDWAYPOINT table:
Abe 18 – Boker Tov- Level 3 (100 points)
Within the last month before Abe got arrested (and his device was extracted), Abe used to wake up naturally however, there was one day the phone woke him up instead. What was the day and (local) time?
Answer: 2023-06-16 06:00:00
There are two ways to tackle this question. The first, and by far the easiest, is to examine the Timeline for Abe’s phone and filter the Description column by the word “alarm,” which returns 52 results. Scrolling down to 2023-06-16 find a Device Notification that is an alarm. The notification occurred at 10:00:00 UTC.
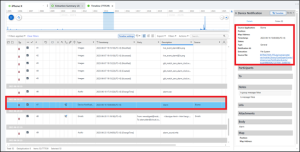
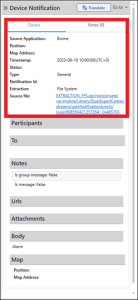
The second way is via Unified Logs, which requires some extra work. To find the appropriate event look for the one instance where the Message column has “MTAlarmScheduler – Firing Alarm.”
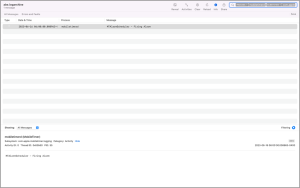
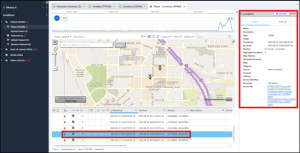
The timestamp in the Biome is in UTC, so we still need to determine where Abe’s phone was on June 16th. Ultra’s Location tab comes in handy here. Under the Visited section of the Locations tab is “Places.” Filtering the timestamp column for June 15th and June 16th finds that Abe’s phone was in Atlanta, GA in the United States when the alarm notification occurred. At that time of year, the time zone offset was UTC -0400, which means the alarm occurred on 2023-06-16 at 06:00:00 UTC -0400.
We hope you enjoyed this CTF. Please feel free to provide feedback on your experience and feedback on PA Ultra to ctf@cellebrite.com. Stay tuned for our next CTF in 2024!