iOS Stolen Device Protection
iOS Stolen Device Protection
When Apple rolled out iOS 18, they introduced Stolen Device Protection. The release of this new capability was meant to prevent device theft, however; it created some serious implications to Digital Forensics practices.
What changed?
Before iOS 18, the passcode was all you needed to ‘trust’ a computer when connecting the device, now Face ID or Touch ID biometric authentication is required.
This is important when conducting Advanced Logical extractions which leverage the iTunes backup protocol. This protocol requires the user to authenticate and ‘trust’ the computer prior to doing the extraction. This can be a problem for numerous use cases where a consent-based Advanced Logical extraction is conducted, and the owner is not present.
This doesn’t only apply to Cellebrite, but any extraction tool leveraging this iTunes back up protocol to extract data.
What can you do?
It’s worth mentioning that Stolen Device Protection mechanisms do not impact Inseyets UFED access methods for iOS FFS when the passcode is known. But if you’re not an Inseyets.UFED user, there is a way to work around the update.
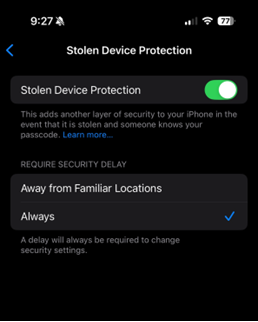
iPhone users can disable Stolen Device Protection on the device through Security Delays, which prevents immediate modifications to settings.
If a user did not modify any of the default settings, there is a time delay of one hour if the user is not in a “familiar location.” This means if the setting is changed, Face ID or Touch ID biometrics authentication is required to complete the process. When selecting it initially and then afterwards.
What is considered a “familiar location”?
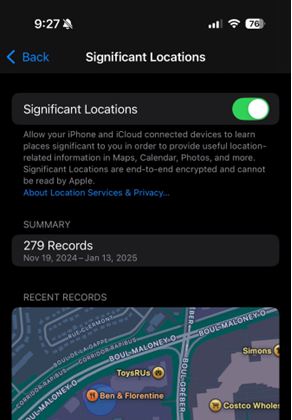
While it’s not specifically tested, there is a mention of Significant Locations in the Apple documentation online, so it can be safe to say it’s likely Significant Locations.
If you are interested in Significant Locations, you can find the information in these files in two different databases: Cloud-v2.sqlite and local.sqlite which are stored in;
/private/var/mobile/Library/Caches/com.apple.routined
Unless you are in a familiar location that is logged in the device, you must wait for the time out period. It’s not likely that a device being extracted by an examiner is in a known Significant Location, unless it’s a test device.
View from the examiner’s perspective — Anticipation is the key for success
Think of this from a consent extraction scenario.
A consenting person gives you a cell phone to be extracted and examined, but they have SDP enabled on the device. You have their passcode for the device, but you will need their biometrics authentication to disable SDP. This means you will have to wait for the time out period.
If you do not disable SDP, and it is activated on the device, you will not be able to extract the data using the methods using the iTunes back up protocols.
What can you do?
- Be prepared
- Anticipate a longer time of extraction process
- If able, have the phone owner disable SDP
- Document the changes
- If possible, conduct extraction of the device at their location(s)
Want tips and tricks and a quick place to get all kinds of best practices? Join The 101, Cellebrite’s user community – a one-stop-shop for all things digital forensics!