What Can Be Recovered From BFU Data Collection
When an iPhone is seized, measures should be taken to ensure that the maximum amount of data can be extracted from the device. An iPhone has two states: After First Unlock (AFU) and Before First Unlock (BFU) extraction.
When in AFU iPhone state, the device has been unlocked at least once after it was powered on. In this state, tools are able to collect a lot of information from the device. If the phone is turned off or loses power, it will revert to the less helpful Before First Unlock mode. Without the user password, BFU iPhone data collection is all you’re going to get.
BFU extraction of data, obtainable with Cellebrite Premium, should theoretically contain only system data. This limited data collection does contain mostly system data but also contains some good user data mixed in as well. The challenge is to locate and interpret what user data is present.
iPhone Data Collection in KTX Files
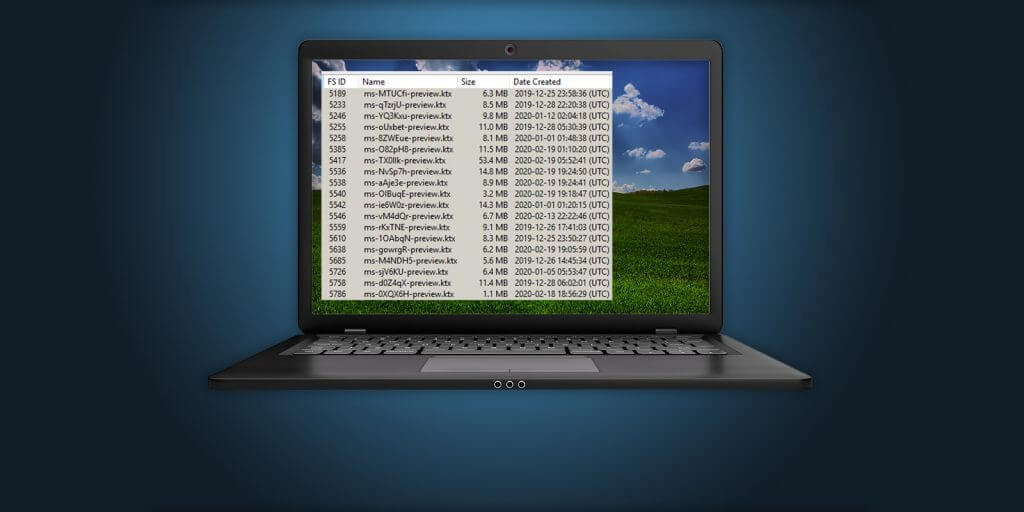
Some user data seen in data collection files are contained in.KTX files. KTX files appear to be a proprietary method Apple uses to show the thumbnail version of background apps or SMS attachments.
Ingesting the data collection with Cellebrite Blacklight 2020 R1 allows you to filter for .ktx files.
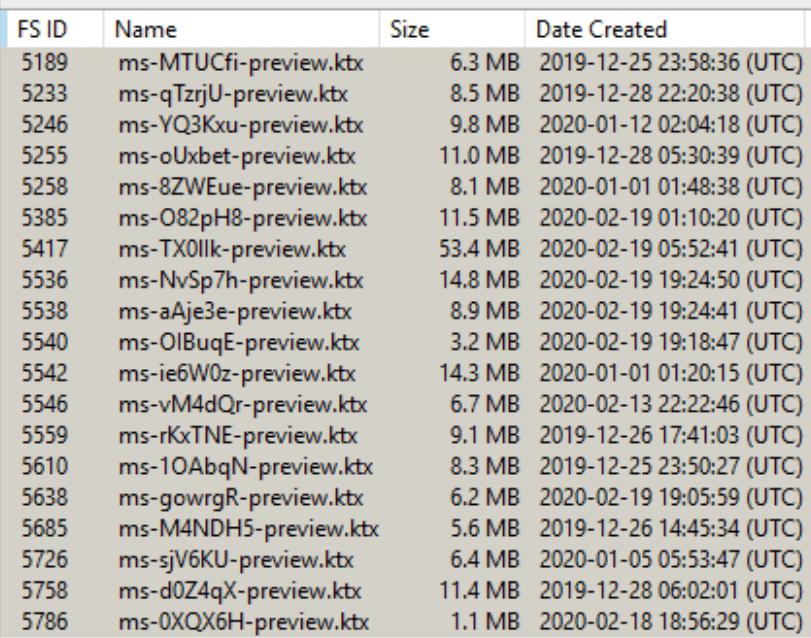
Both system and non-system .ktx files will be shown. You can differentiate the two by looking at the path.
Non-system .ktx files, which have the potential for containing user data, are typically in paths like:
/private/var/mobile/Library/Caches/com.apple.MobileSMS/Previews/Attachments/ b7/07/1C495ABD-6D72-4E67-BCF0-61D3CD9B0EA8/ms-M4NDH5-preview.ktx.
System-generated .ktx files are stored in Framework paths. For example:
/System/Library/PrivateFrameworks/AssetViewer.framework/PlugIns/ASVAssetViewer.appex/studio_lighting_armode_specmap.ktx
/System/Library/Frameworks/RealityKit.framework/studio_lighting_armode_specmap.ktx
When you select a .ktx file, the File Content Viewer will not display the file. This is because there is a leading 8-byte hex string before the normal .ktx file header (<<KTX.11>>):
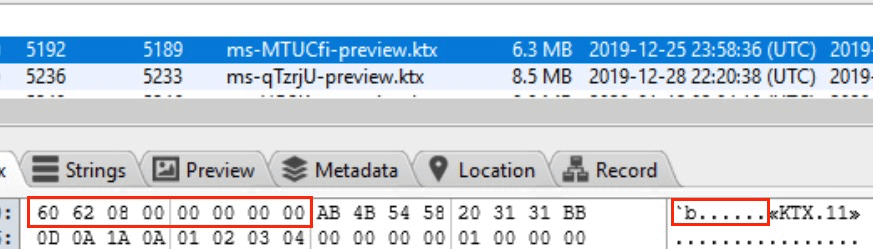
Exporting the .ktx files and loading them in Photos in macOS will also not work because of this erroneous 8-byte string. So, how do we look at the data?
Perform the following steps to view the .ktx picture:
-
- With the .ktx file highlighted in the Content Pane, select the Hex tab in File Content Viewer.
- In File Content Viewer, highlight (select) all the data contained in the file with the exception of the first 8-bytes.
- Command-click on the highlighted data in the File Content Viewer and select Export, Export Selection, Raw Data….
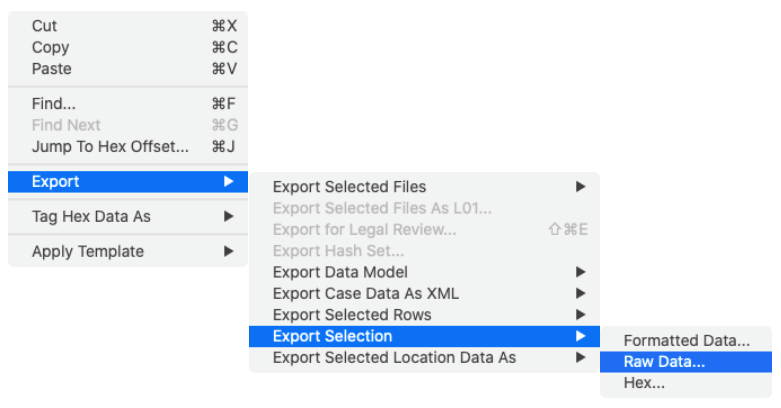
- A Save dialog box appears. Provide a name for the file. The new file will contain the data from the original file, minus the erroneous 8-bytes.
- Open the new modified .ktx in macOS. The .ktx can be converted to a .JPG.
- With the .ktx file highlighted in the Content Pane, select the Hex tab in File Content Viewer.
Other Information that Could Be Useful for iPhone Data Recovery
You may find other information in Before First Unlock extraction for data collection that is relevant to your investigation. Keep in mind that many users store information, and possibly device backups, in iCloud. You may potentially find information allowing you to apply for a search warrant for iCloud information. Refer to the following locations to find iCloud data:
-
- Last Cloud Backup Date: /private/var/mobile/Library/Preferences/com.apple.mobile.ldbackup.plist
- Last logged-in user Directory Service Identifier (DSID): /private/var/mobile/Library/Preferences/com.apple.corerecents.recentsd.plist
- iCloud Configuration Information: /send memes/private/var/mobile/Library/Preferences/com.apple.storebookkeeper.plist
- Cloud Sync Enabled and Cloud Sync Enabled Modification Date: /private/var/mobile/Library/Preferences/com.apple.assistant.backedup.plist
- Home Sharing Apple ID: /private/var/mobile/Library/Preferences/com.apple.homesharing.plist
- iCloud Sync Information: /private/var/containers/Shared/SystemGroup/systemgroup.com.apple.configurationprofiles/Library/ConfigurationProfiles/CloudConfigurationDetails.plist
Finally, two other locations that may contain user information in BFU data collection:
-
- applicationState.dndb: /private/var/mobile/Library/FrontBoard/applicationState.db
- Snapchat primary.docobjects database containing contact information:/private/var/mobile/Containers/Data/Application/B65F45DF-09DB-4510-9E04-D8C5D5AF9DF7/Documents/user_scoped/4f865e4901fcb2103db07ff946a974ecf0094545050a837c45d7f224e58c4892/DocObjects/primary.docobjects
Remember, if you seize an iPhone and it is already powered on, try to keep it that way. This will ensure you can get AFU iPhone data collection. However, if your only option is BFU iPhone data collection extraction, take a good look at the information. Some user data typically is mixed in with the system information. It may be enough to provide new leads for your case.