How to use Cloud forensics tools in Physical Analyzer

This week’s Tip Tuesday covers cloud forensics tools in Physical Analyzer which you can use to perform lawful extractions on private and public cloud data.
Disclaimer: Make sure you have legal authority or consent. Credentials are needed for extraction.
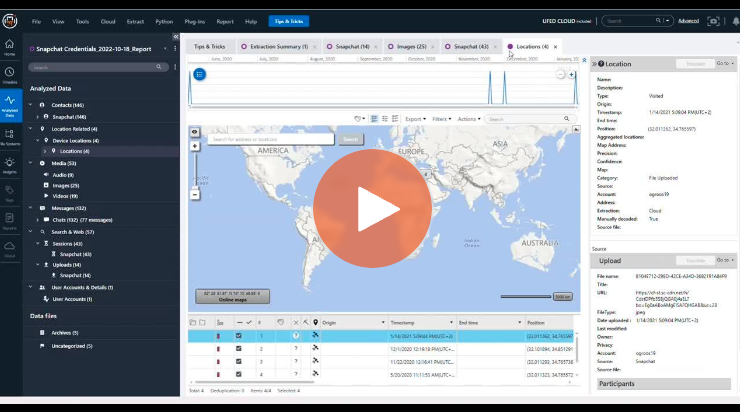
With credentials, you can extract a vast amount of information from location data to media files. (Shown on the left-hand sidebar).
User-uploaded media such as My Eyes Only artifacts can only be extracted in specific cases where the needed key is on the phone. Only associated metadata will be shown if the credentials or needed key is not present.
Chats can also be extracted if they are still present on Snapchat’s servers.
Note: If you’re doing full cloud extractions, typing ‘Snapchat’ on the top area may limit your search in the analyzed data view.
Watch the video to find out more.