How to Use Samsung Rubin Data in Your Mobile Device Forensic Tool – What You Need to Know
What is Samsung Rubin?
Samsung Rubin is the customization service available on newer Samsung devices that can log valuable data which can be lawfully accessed using a mobile device forensic tool during a digital investigation. There are many ways to activate this service. The primary way to enable customization is to: Go to Settings > General Management > Customization Services. Other ways to enable the service may include enabling it during the creation of a Samsung account on the device by going into Privacy settings or the Digital Wellbeing settings. A user can select the customizations they want to include. You may find that some users enable these customization services by accident and are not aware of the logs keeping tabs on the device. Keep in mind, these settings will impact what Physical Analyzer can parse, assuming the proper full file system extraction has been leveraged.Why would a user enable customization?
The following are the benefits of customization a user will see on their device:- Personalized content based on device usage
- Direct marketing based on your interests
- Customized ads
- The ability to locate your device should it go offline
- Device Connectivity, such as WiFi
- Samsung Browser searches
- Samsung Browser history
- Location information
- And more
How can this data be leveraged using an Android Mobile Device Forensic Tool?
For the digital examiner, the data collected from a Samsung customized service can produce a wealth of evidence from charging states to application usage data. For those familiar with iOS forensic examinations, Samsung Rubin is the closest thing that we have to the KnowledgeC database, acting as the tracker of truth. Questions that could be answered include:- What was the user doing in Samsung browser?
- Was the device on or off?
- Was WiFi in use?
- Where was the device when an activity occurred?
Diving into Samsung Rubin Digital Artifacts
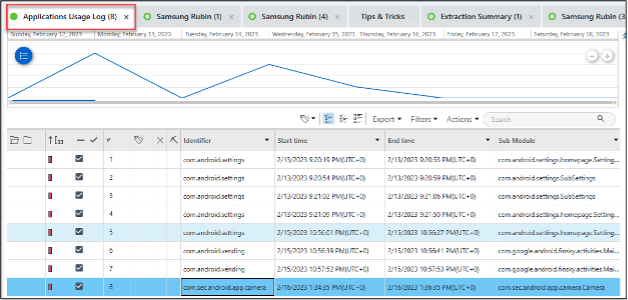
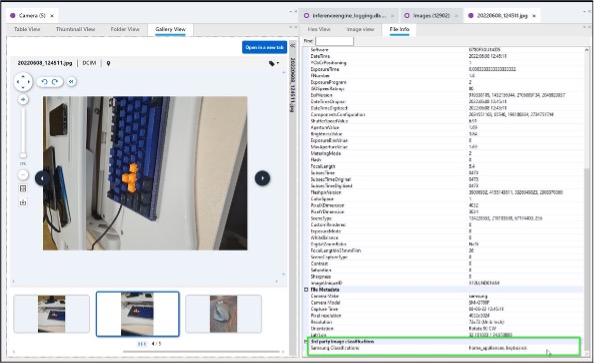
There are two key files of interest discussed in this blog. The first is /data/data/com.samsung.rubin.app/databases/inferenceengine_logging.db View the screenshots below for reference:- Application usage
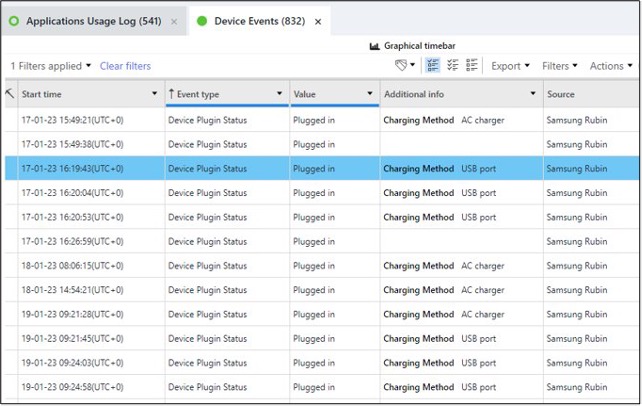
- Charging state
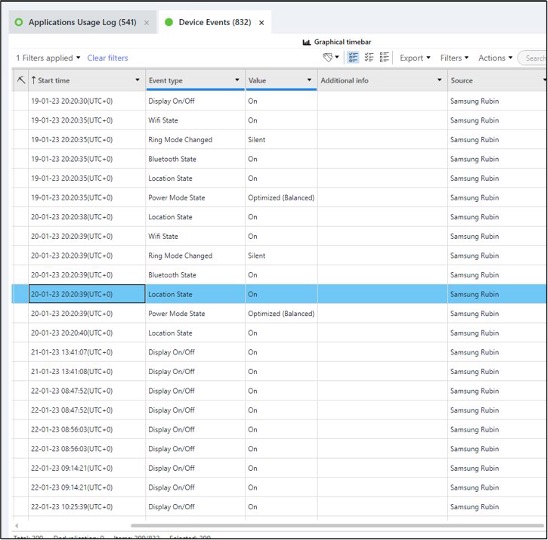
- Device events
- Location services on/off
- Ringer state
- Display on/off
- Many more
- Location data

- Media Categorizations (Samsung Native)
- Details are in the File Info – showing the categories
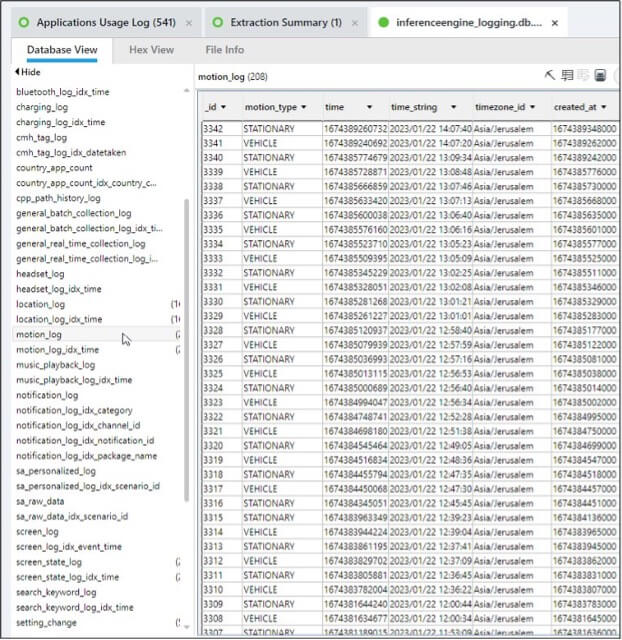
- Motion log
- Vehicle moving/stationary
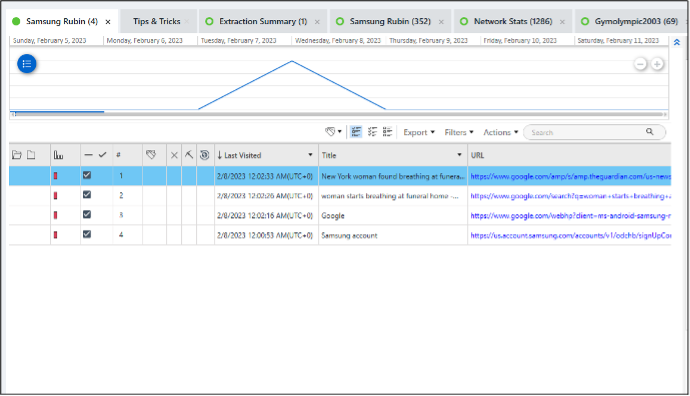
- Samsung browser search query
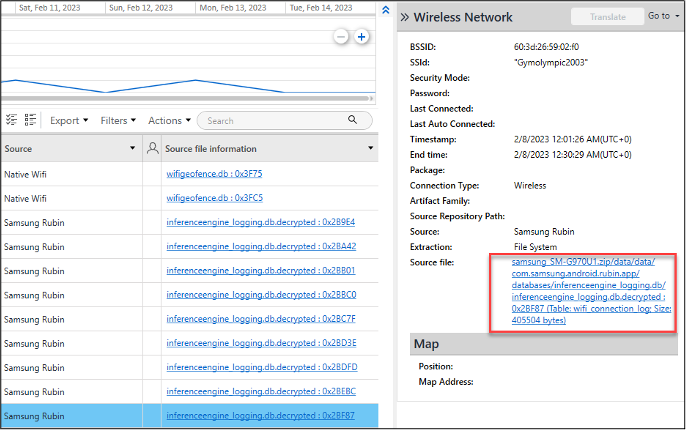
- WiFi connections
- Bluetooth Connections – from the all_bluetooth_log table
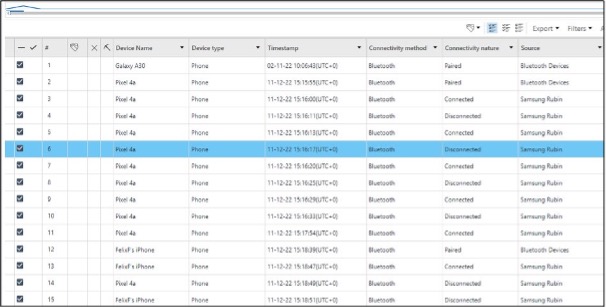 The second file is located at: /data/data/com.samsung.rubin.app/databases/inferenceengine_monitoring.db.
The table analyzed_place_monitor displays the user’s main frequented locations (home, work, etc.) and their coordinates in terms of latitude/longitude.
The second file is located at: /data/data/com.samsung.rubin.app/databases/inferenceengine_monitoring.db.
The table analyzed_place_monitor displays the user’s main frequented locations (home, work, etc.) and their coordinates in terms of latitude/longitude.
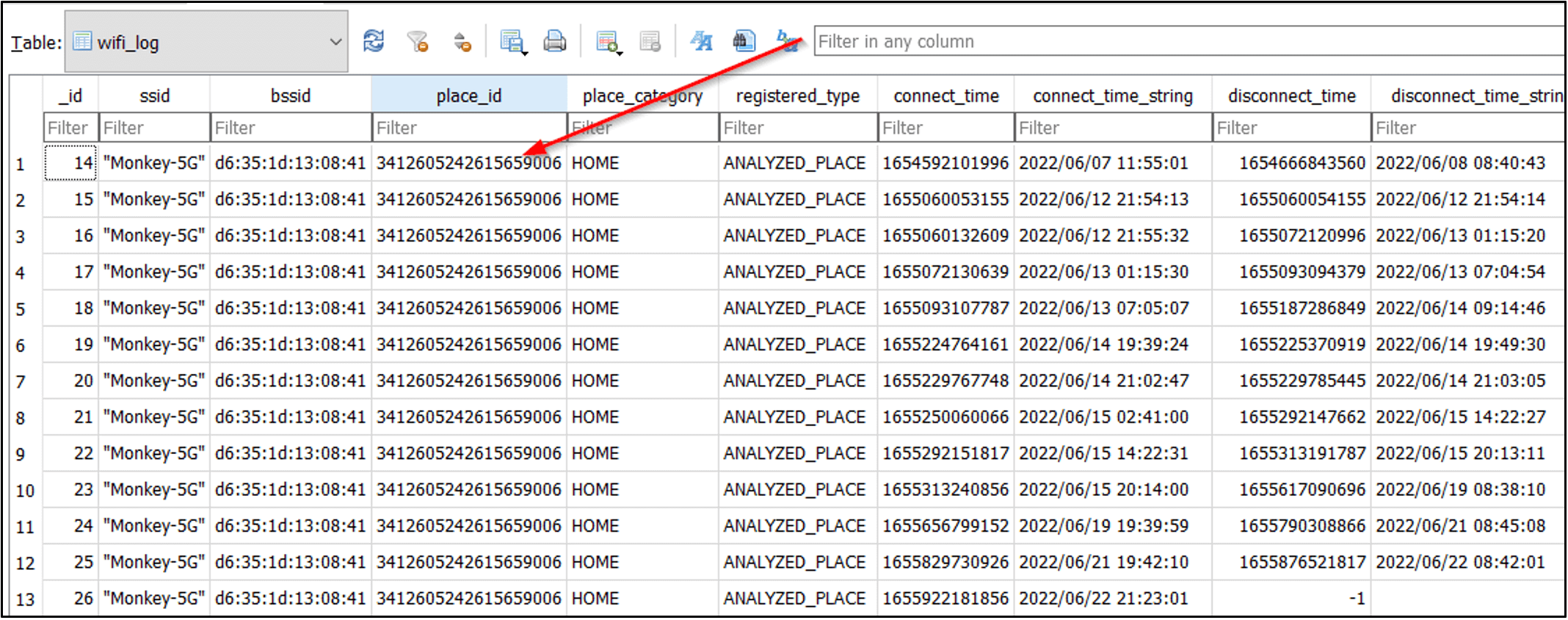
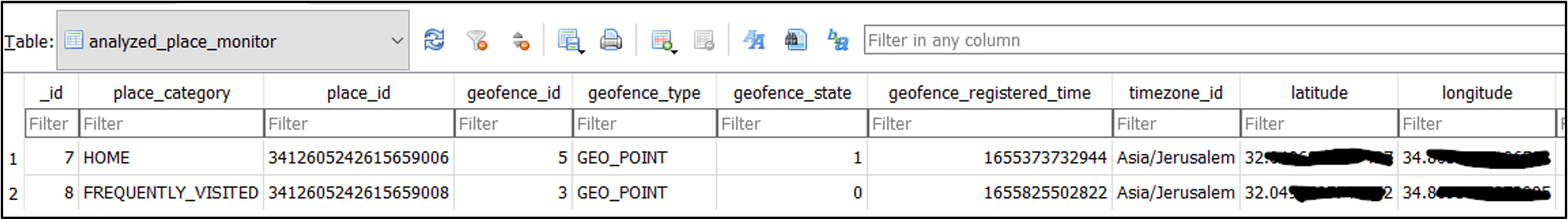 The value inside the place_id column is then used in other tables in the inferenceengine_logging.db to identify the coordinates. For instance, the wifi_log table contains additional artifacts.
The value inside the place_id column is then used in other tables in the inferenceengine_logging.db to identify the coordinates. For instance, the wifi_log table contains additional artifacts.
Top things to remember about Samsung Rubin:
- The data will not exist forever – The data in db will typically last for only 30 days.
- Location artifacts from Samsung Rubin are locations the device visited.
- A Full File System or Physical extraction is required to parse Samsung Rubin.